Greetings within our regular networking and cybersecurity newsletter! This time are going to have a closer look at articles and academic papers published between July 27 and August 1, 2020.

Greetings within our regular networking and cybersecurity newsletter! This time are going to have a closer look at articles and academic papers published between July 27 and August 1, 2020.
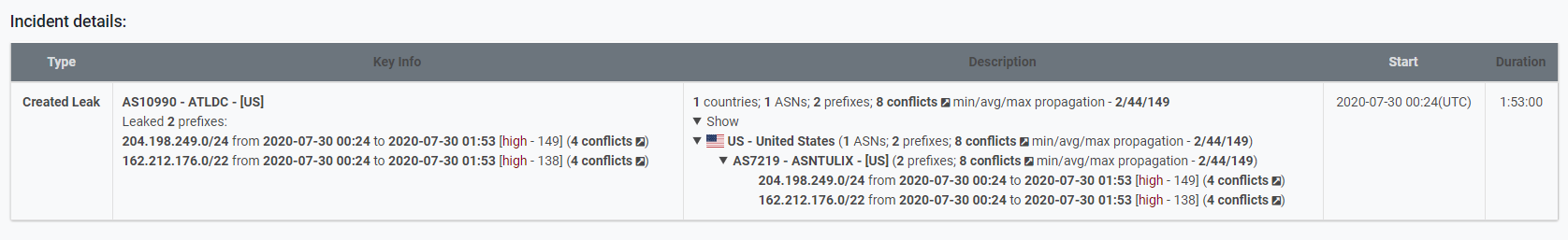
On the border of July 29 and 30, depending on where in the world you were, a routing anomaly occurred. Following the NANOG question regarding what exactly was happening, Qrator.Radar team loaded the researching instruments and dived into the investigation. Nevertheless, before we start, let us take a general overview of that play's main actors.
Welcome to our regular weekend newsletter containing every remarkable story on networking and cybersecurity published between July 20 and 25, the year 2020.
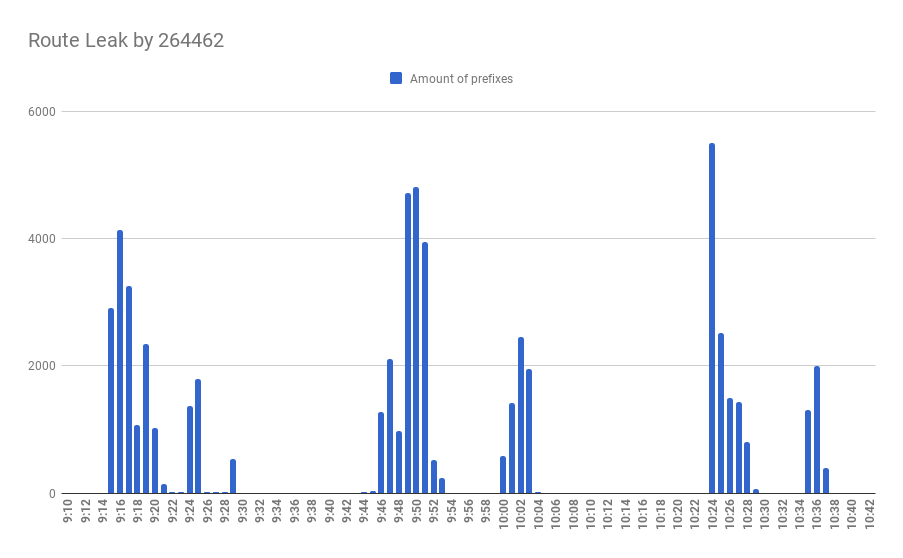
In the morning of Tuesday, July 21 a Brazilian AS 264462 belonging to “Comercial Conecte Sem Fio Ltda me” as it is stated in the whois record for this particular ASN, leaked massive 13046 network prefixes in a networking incident that lasted for 1 hour and 23 minutes, starting at 9.15 UTC and ending at 10.38.
As always, greetings within the latest cyber- and networking security newsletter brought to you by Qrator Labs. This time we are going to take a look at the most important and relevant stories published between July 13 and 18 of the year 2020.
Hello and welcome to our weekly recap of the news and articles worth attention on the topics of networking and cybersecurity published July 6 to 11, 2020.
Ladies and gentlemen, after a short vacation, we are back with the most relevant and essential news on cyber and network security.
This time we are going to make the 2-week overview, covering stories published roughly from June 22 to July 4. Enjoy!
Here we are again with the newest information on what happened in cyber and network security from June 15 to June 20. There has been a lot of events, so let's roll with the most critical ones.
Wow, that's been a week! Here's the blogpost copying our newsletter that covers all the newest information on what happened in cyber and network security from June 8 to June 13.
There would be no TL;DR in this article, sorry.
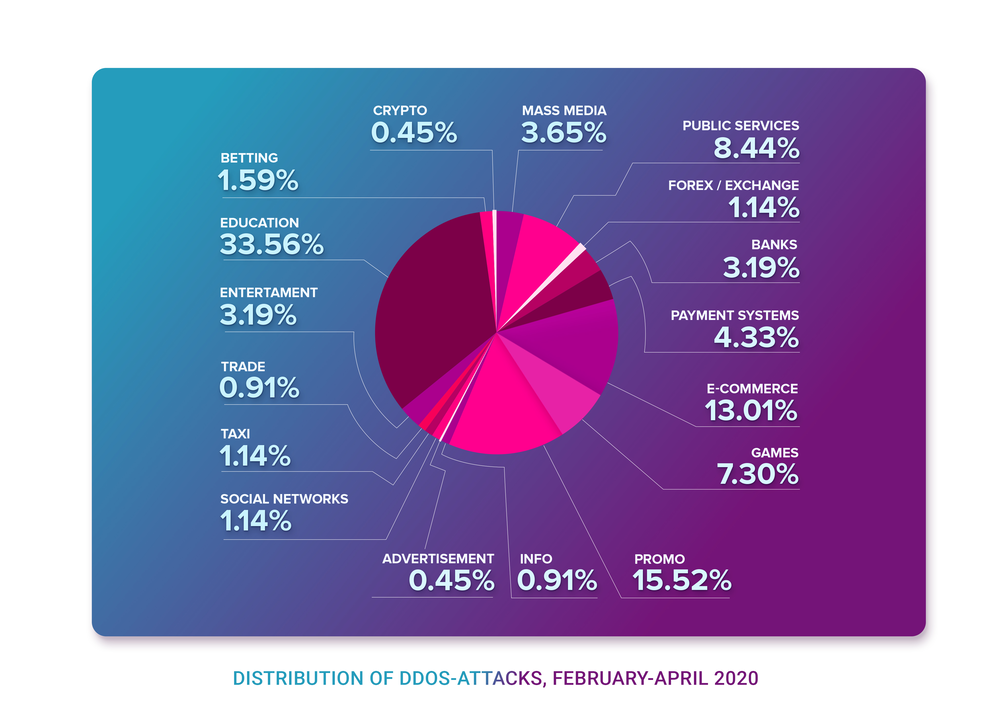
Those have been three months that genuinely changed the world. An entire lifeline passed from February, 1, when the coronavirus pandemics just started to spread outside of China and European countries were about to react, to April, 30, when nations were locked down in quarantine measures almost all over the entire world. We want to take a look at the repercussions, cyclic nature of the reaction and, of course, provide DDoS attacks and BGP incidents overview on a timeframe of three months.
In general, there seems to be an objective pattern in almost every country’s shift into the quarantine lockdown.