Recently, several severe routing incidents were spreading globally: hijack of the 5% of an entire IPv4 address space from Brazil, route leak between Russia and Asia through Kyrgyzstan, and at last, previous Friday there was an event that could lead to an outage of a significant part of all the BGP ecosystem. Fortunately, it didn’t happen.
18th May at 9:36 UTC, a Brazil ISP, named PBNET (AS263086) started leaking thousands of prefixes between its upstreams: TELY (AS53087), and OPENX (AS263444). Two waves lasted for about half an hour, as number of affected prefixes reached nearly the size of a full BGP table. This leak was accepted and propagated by the OPENX. In the case of its acceptance by the bigger networks, which have proved to have poorly maintained filters, this particular leak could have had a dramatic impact by redirecting a massive part of the world traffic to the small transit ISP.
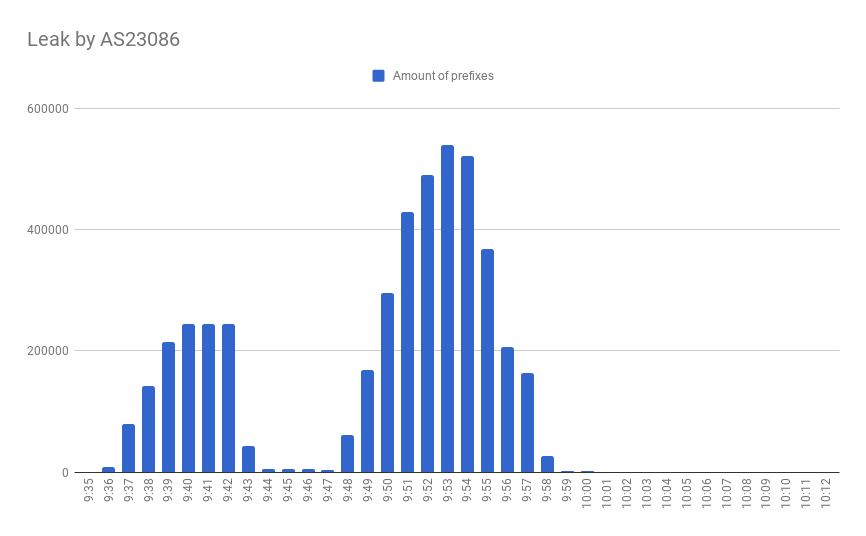
But we are fortunate that the upstream provides of OPENX: NTT (AS2914) and EDP4 (AS22356) are using IRR filters based on the AS-SETs, resulting that only a limited amount of leaked prefixes became globally propagated. The ideal IRR filters represent routes from an AS cone: prefixes that belong to direct and indirect customers of an AS operator. Such filters, still, might be bypassed by route leaks or hijacks that are happening inside its customer cone, but more importantly, design limitation is that anyone can add anything in own AS-SET. Such outdated or malformed AS-SETs make the effort of implementation of IRR filters significantly less effective.
Still, this leak significantly disrupted Brazil internet segment, and more than 5000 prefixes were propagated globally due to the structural limitations of IRR filters. Most of this prefixes belong to Brazil ISPs, but there were also CDN networks, such as Akamai. However, the consequences of this routing incident could be much worse.
