For the last 30 years basic idea behind the Internet’ design hasn’t changed - it connects people and services with each other. However, some authorities may have a different angle on what services their citizens should be able to connect to. A regulator might require ISPs to block off selected content or IP-address space for the end-users. How is that implemented? There are many options, but the most popular one is with the help of static routes, that may be propagated locally in BGP. Mistakes in this ‘local propagation’ have happened before: most notable was the YouTube hijack back in 2008, but less famous events were continually happening all over the decade. Today we observed another one, created by Iranian ISP that affected Telegram messenger.
While BGP was invented to maintain openness over the Internet, it becomes popular for the censorship purposes. Openness and censorship are two conflicting goals, and we are not sure if Bolivar can carry this double. What happened today (it’s a hypothesis, we can’t be 100% sure on the outside) was a leak of static routes to the BGP made by TCI (AS58224). The resulting hijack affected 9 ASNs, including Iranian, Russian and UK networks - all those seem to be regular static routes. It also affected 3 prefixes that belong to Telegram, which use is officially restricted in Iran.
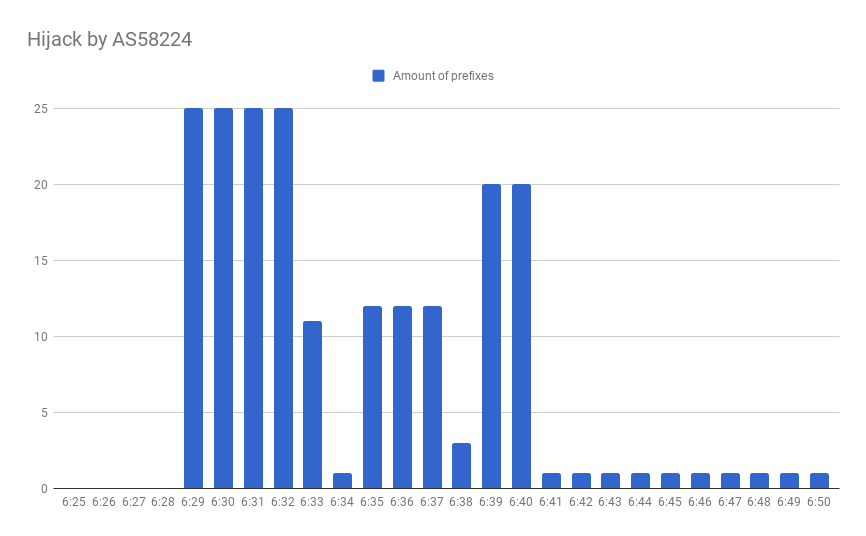
The problem was not the configuration mistake in the TCI network itself, but the absence of filtering at the transit ISPs level, which resulted in propagation of these invalid routes globally. There were several responsible transit ISPs advertising these invalid routes, including two Tier-1 ISPs: TATA (AS6453) and KPN (AS286) accepted hijacked routes from its customers, while, for instance, Telegram ASNs are not listed in corresponding AS-SETs. Ingress filters quality at these networks may require further investigation.
