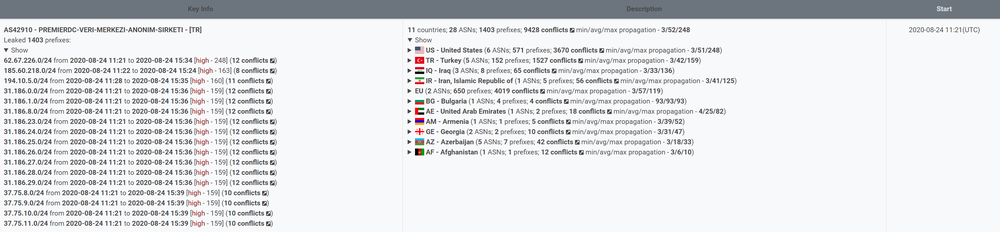
Yesterday, on August 24, 2020, Qrator.Radar BGP monitoring saw a rather large route leak originating from the AS42910 - Premier DC, containing 1403 prefixes mainly from the United States (571) and, peculiarly, Akamai. And then almost all the Western Asia region countries.
The incident started at 11:21 UTC and contained four distinct waves, ending only around 16 UTC.
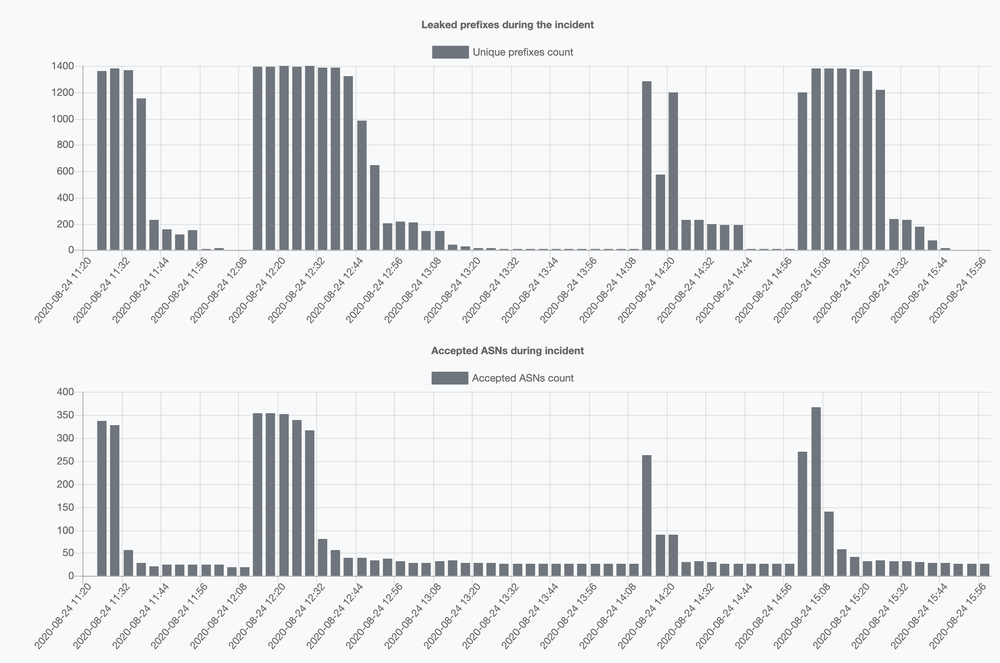
We can state that in total, this particular routing anomaly lasted for more than 4 hours, repeating several times - with success in effect. And this is what differentiates this yesterday’s route leak from what we usually see - one massive leak weakening over time.
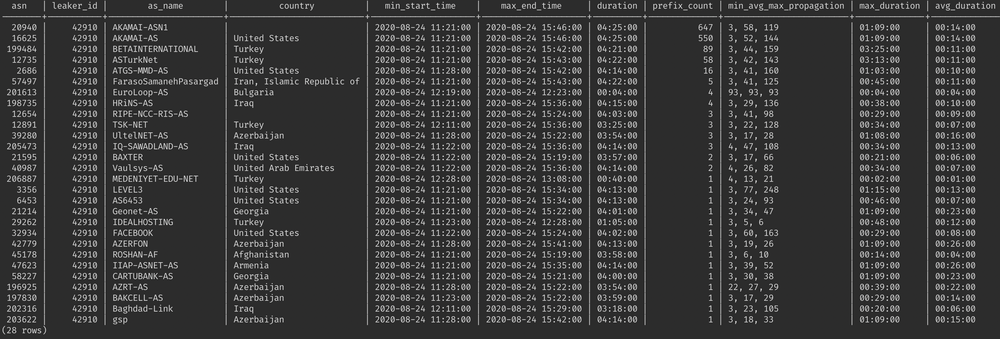
Furthermore, what is even more intriguing is that more than one thousand of those 1403 prefixes in the leak belongs to Akamai - one of the more prominent Internet players.
However, this particular anomaly spread from AS9121 to AS61135 - and even AS-SET based filter on the side of AS61135 would not save it from being unwillingly propagating the leak further - because leaker AS42910 included all directions into its AS-SET.
We do not know precisely what happened inside the 42910 network, though it looks like it does not have any form of rate limit installed as the leaks were significant. And, again, the repetitions of the same ejection are rare, according to our experience.
We would leave the article without conclusion. Take care of your network.
