The situation we observed last week was both peculiar and strange when panic for Cisco Smart Install Protocol remote code execution vulnerability (cisco-sa-20160323-smi) started circling. There was confirmed botnet activity that was wiping configuration files exploiting this vulnerability and leaving a message “Don’t mess with our elections.” Moreover, there were rumors that significant amount of ISPs and even Internet segments get down due to this malicious actions.
At Radar.Qrator we made our best to clear things out and got everything straight without emotions. The first observation that we made was that level of drama exceeds the level of problem. We checked traffic values for Qrator, for major IXes - there was no clear evidence. We also checked the number of BGP sessions of Radar; they also were not affected. The best view on the problem was found using cird-report:
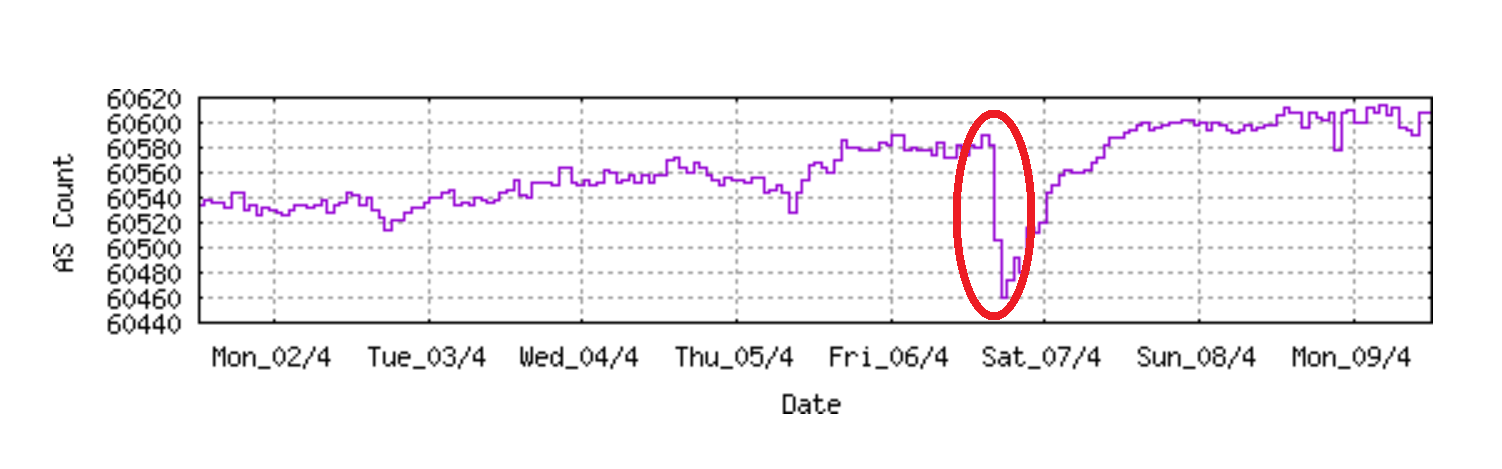
So, the malicious attack seems to simultaneously hit about a hundred ISPs at Friday evening, the majority of them belong to Iran. So the curious thing that we were lucky. Lucky that these Cisco switches are not widely used as border routers. We were also lucky that this bot was only wiping configuration instead of hijacking half of the world.
Again, that highlighted the problem that routing hardware has open ports that can be easily reached by attackers. It is important to apply the patch to fix this vulnerability, but this patch does not create ACL filters to close 4786 port. The Cisco (or any other hardware vendor) control plane is not supposed to withstand any attack that exceeds 1 Gbps of traffic. Moreover, tomorrow this routers and switches may get down again due to SYN flood with very same results. Even worse.
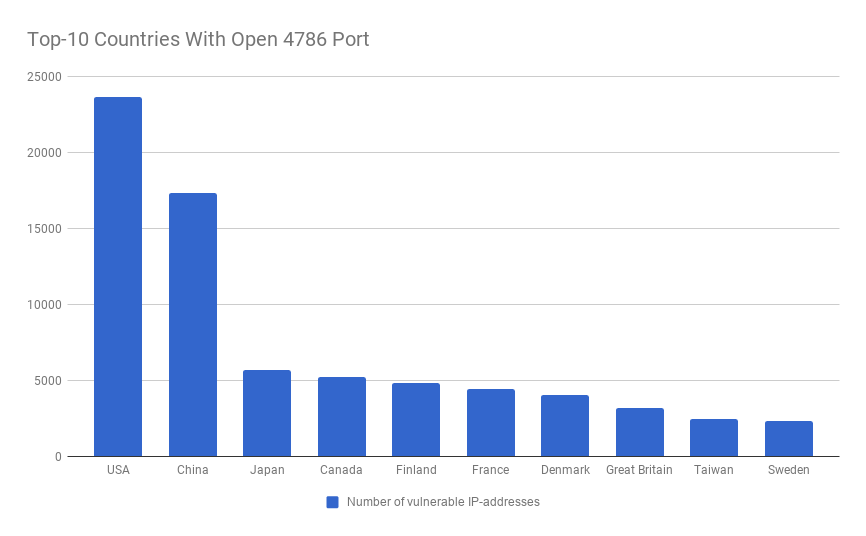
According to our research, there are more than 100 000 devices in the world with open 4786 port. They belong to nearly 5000 different ASNs. We also mapped these devices to countries. The top-10 looks as follows:
As a reaction to this threat, we have added detection of Cisco SMI port in our scanning measurements. We encourage our users to check ‘vulnerable ports’ section of your AS registered within the Radar to be entirely sure you are not affected.
