There would be no TL;DR in this article, sorry.
Those have been three months that genuinely changed the world. An entire lifeline passed from February, 1, when the coronavirus pandemics just started to spread outside of China and European countries were about to react, to April, 30, when nations were locked down in quarantine measures almost all over the entire world. We want to take a look at the repercussions, cyclic nature of the reaction and, of course, provide DDoS attacks and BGP incidents overview on a timeframe of three months.
In general, there seems to be an objective pattern in almost every country’s shift into the quarantine lockdown.
Spin Down
As the epidemic measures tightened, the transport and logistics (and tourism which is not possible without those) were first to get under stress, because people were massively cancelling or rescheduling their travels, deliveries, shipments and dispatches in coordination with countries closing or restricting the borders crossings. Taxis also felt the overall activity drop.
It is not surprising that almost simultaneously, there was another layer where, contrarily, activity spiked tremendously: in stock, equity trading and currency exchange. Indeed, this is an industry that “buys the rumour and sells the news” as it were the traders who reacted to the changing world blazingly fast. And they still do, because they operate on both downward and upward movements of the price. Traders were among few professions over the Internet that had much more work and opportunities during those three months.
As a next stage after-effect to shutting down the transportation and especially the events hosting lots of people (or should we rather say, shutting down virtually every event that takes place in real life), all the ticketing, reservations making and other venue activities-related services fell a considerable drop in their web attendance. And they are recovering very slowly because the difference in lockdown measures complicates international events, most borders are still closed and also by the fact that in quite a few countries the comeback of festivals, concerts or even theatrical performances is already planned. Those industries are trying to adapt to such new realities, and we don’t know yet how it would turn out for them, especially for the hoteliers and short-term rentals markets, that were strongly affected.
As a result of economic shocks and the rise of unemployment, as well as cancelling almost all sports activities, this is probably the worst time for betting. This time it combined several factors so crucial for the willingness of people to bet their money on something other than their health.
Spin Up
On the other hand, we have some industries and economic sectors that benefited from what was happening, although it is not clear if they could capitalize on achievements.
Mass media and social networks are among the ultimate winners. In the situation of stress, many people turn to news and stories sources, and we have seen how different the reaction could be, especially in self-managing communities, like Wikipedia. People need a source of information, and during those three months, we saw how active users grow on most of the general-themed news sites, but not exclusively. And many tried to exploit the information thrust to their advantage using all kinds of shadowy techniques like click-baiting, or even worse.
Our friends at Habr.com showed us how tremendously Coronavirus pandemics changed the way people react and respond to specific stories. There was a single post that gathered the attention of millions of people, seeking data on the ultimate topic we had in those three months.
(Habr’s CDN stats for February and March 2020)
At the same time, online education and online streaming services, as well as gaming platforms and communities, skyrocketed. And with the streaming services, even local governments reacted with their requirements to lower the video quality for traffic optimization, and ultimately, that was complied with by the largest players, like Netflix and YouTube. The same download speed throttling came to the most significant game marketplaces, like PlayStation Network, while Steam was reporting a concurrent players peak.
You’re probably wondering here how we dare to mix education with entertainment.
Well, it seems that edutainment exists on the Internet. During this period, we saw how educational services, by opening their courses for free or with a discount, experienced tremendous growth in users and visitors count. As schools, universities and some offices were shut down for physical attendance, pupils, students and even grown-ups were looking for an efficient way to spend their time.
And we know pretty damn well that if you work hard, you can play hard. That is why the gaming and the streaming industries could be those long-term winners because those habits would probably stay with people that got them in those three months.
E-commerce and retail changed immensely over that same period because, for months, the only way to sell something was to sell it over the Internet. We saw how businesses, from small to gigantic, were transforming their operations and tactics towards better efficiency under immense stress. Groceries, wholefoods, butchers, tailors, carpenters and gardeners — everybody had to take adaptation measures to stay with their clientele, not losing old ones and, probably, acquiring new ones. And this particular time, we also see a growth in alcohol retailers traffic growth and a significant drop in office tools retail, both of which are tied to mass migration to home offices.
It was interesting to see how retail and e-commerce businesses were adapting to the fast-growing demand, and “shared” their customers with each other in real-time — as some specific websites got overwhelmed by the visitors and started to choke on resources (whether that were CPU, memory or what we saw as a number one factor — available transit bandwidth), customers immediately reoriented themselves for services that were more readily available, materializing the old proverb “vote with your wallet”.
The same stands for the software we use to communicate with our colleagues, partners, customers and suppliers of all kinds — during these 3 months many companies realized where they actually stand on the security field, as troubles were crippling the reputation of some widely used software products, names omitted.
And probably the last, although not the least thing in our quick introduction, was the pressure which tested every e-Gov service in any region of the world. As people were locked down in their homes, they tried to get ahead of the trouble and make everything possible to be ready for whatever was going to happen. Taxes, courts, appointments with government officials, insurance and hospital services, social services — everything was under fire as people were caught in unpleasant moments and seeking help from their governments.
And it turned out that in most cases the government electronic services could adapt and survive through this high demand, which is excellent and, in best case scenario, would give us new insights in what services we believe and how we can interact with them.
DDoS-attacks

In this section, we want to share with you our insights on how DDoS-attacks evolved and changed during the questioned period.
Please note that this timeL7 (application layer) attacks were intentionally excluded from the overview.
First of all, let’s take a look at the candlestick charts that we’re describing the data with. We would start with the DDoS-attacks duration data for the period from February 1 to April 30.
With these charts, we’re focusing on the median (quartile 2), the minimum/maximum and quantiles 25 and 75.
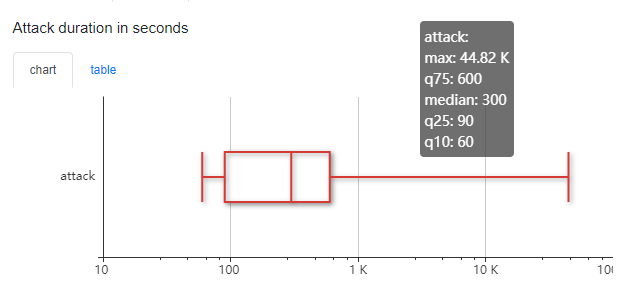
As you can see, the median attack time is 300 seconds — 5 minutes. But the overall distribution in time is broad, with the maximum attacking timeframe of 12.5 hours. Modern attacks are fast and intense, and this doesn’t change with pandemics.
Duration of attacks on different industries
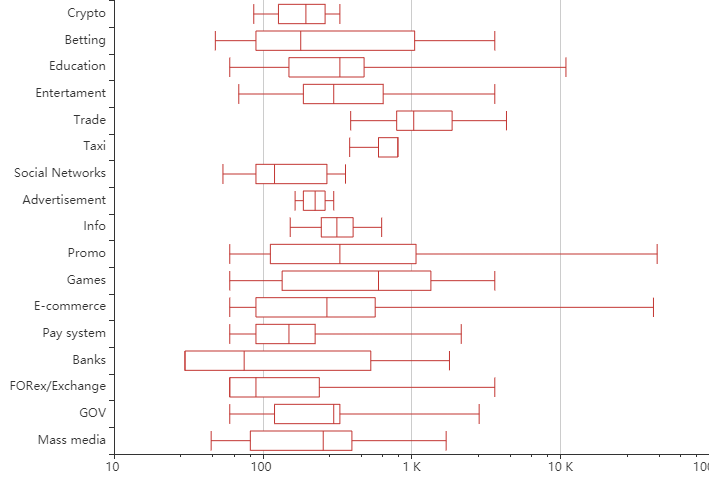
Now let’s take those durations and take a look at how they differ from one client category to another.
It is pretty evident that the promo and e-commerce economy sectors have the most prolonged attacks, with banks having a median of their attacks quite low compared to taxi services or gaming and trade industry. Every industry has its specifics on the Internet, and since a large portion of the DDoS-attacks is unfair competition, you see the difference between approaches.
The bandwidth of attacks on different industries
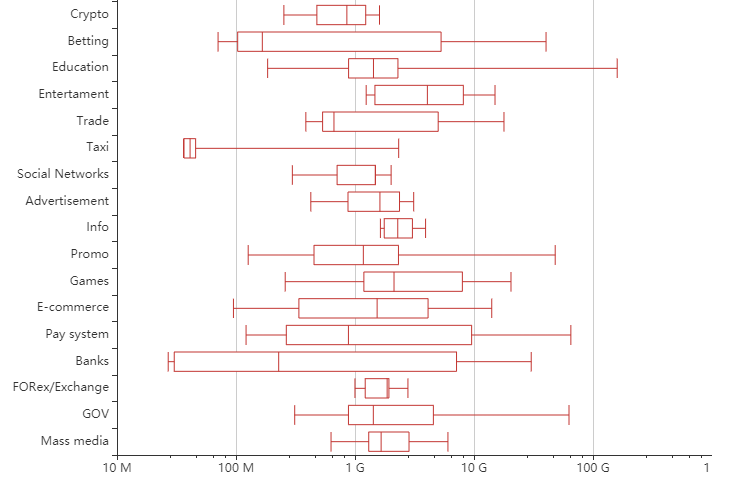
That is the bits per second candlestick chart for the same attacked industries in the questioned timeframe.
As you see the most intense attacks during these three months were targeted at the education sector, followed by payment systems, local governments and public sector services, with promo pages and betting resources closing the top-3. Here the maximum attack bandwidth in the Education sector was targeted at one of our clients opening the educational courses for free, followed by an assault of hundreds of gigabits per second on their resources. Someone else wanted those students too.
Distribution of attack vectors
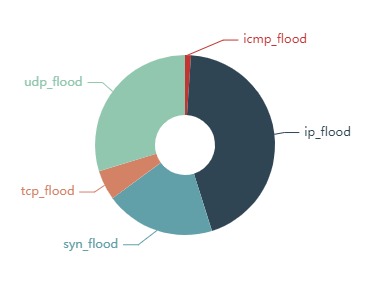
Fragmented IP flood is still the king of the DDoS-attacks mountain with 43,32% of all attacks (though a certain portion of this achievement belongs in fact to UDP amplification attacks). UDP flood follows with 29,37%, and SYN flood closes the top-3 with 19,53% of all assaults.
Duration of attack vectors, seconds
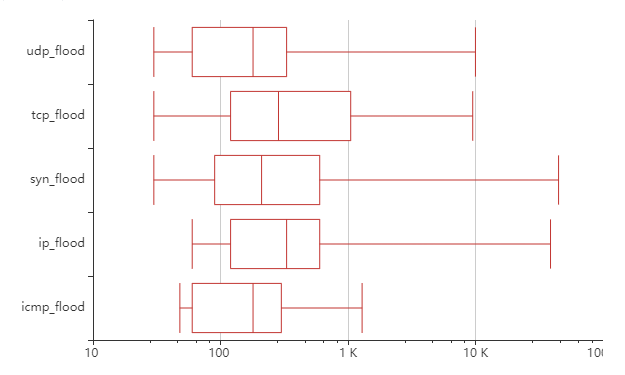
Here we can say that attacking vectors rarely drastically changes the timeframe of DDoS-attacks since those are mostly orthogonal things.
Attack vectors bandwidth and packet rate
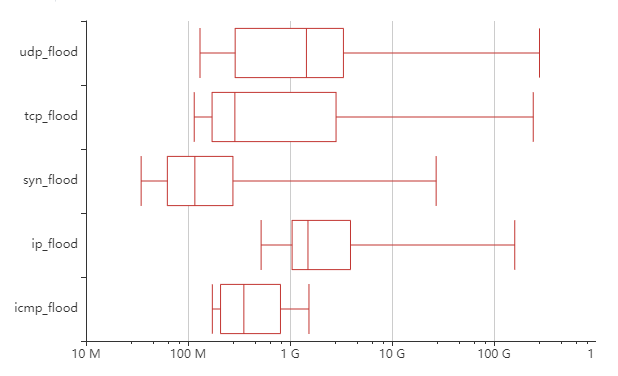
Here we see what was known for a long time — UDP flood has the highest bandwidth median and maximum, followed by the fragmented IP flood. You probably already know that in real attacks that are real threats, several vectors would be utilized in order to maximize the effectiveness of compromised attacking resources.
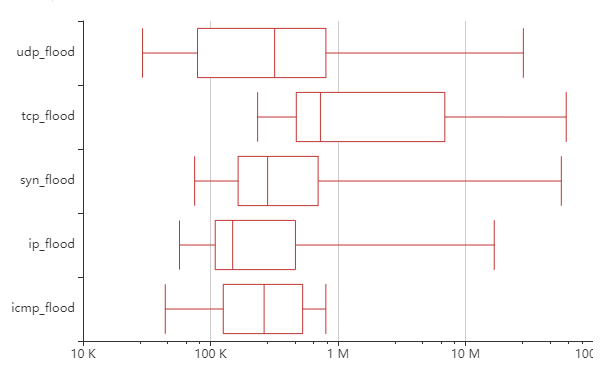
That is the packet intensity (PPS) chart for the same vectors.
And, finally, we have a pie chart of vectors combinations.
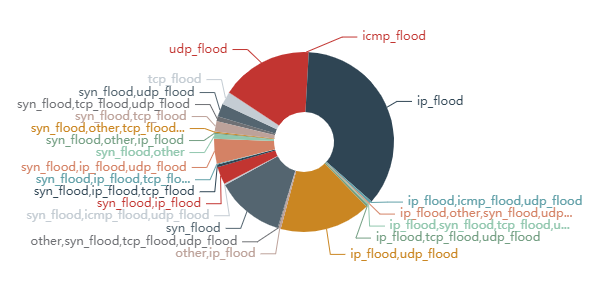
Where you can see that even while the IP flood stands for the most utilized attacking vector with 35,67% of all attacks, after clear UDP flood (with 15,71%) and SYN flood (with 12,31%) the rest 40% is in vectors combined.
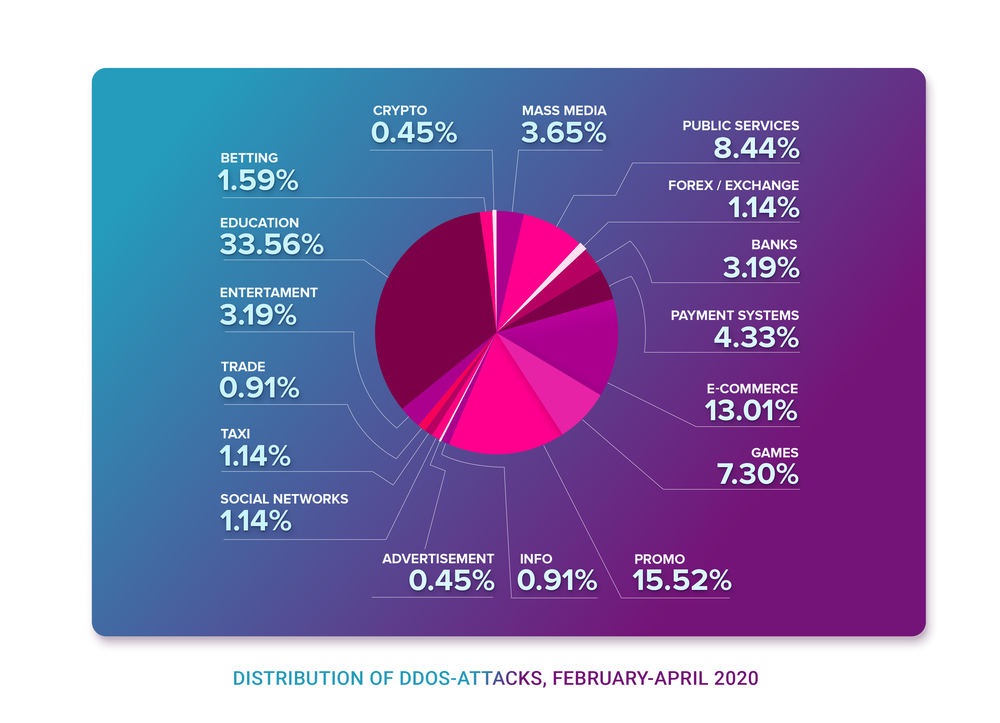
Again, we want to reiterate the chart we used at the beginning of this article.

Here you can see that the most attacked industries during those three months were:
- Education, with 33.56% of all registered attacks;
- Promo, where we count resources aimed at gathering attention in short periods;
- E-commerce (retail) with 13.01% of attacks;
- Public and government services with a little less than a tenth of attacks — 8.44;
- And the top-5 closing with gaming sector attracting 7.30% of DDoS-attacks.
BGP routing
Almost simultaneously with the quarantine measures in each region and country lockdown and migration to home-offices where possible, major Internet exchange points were reporting historical records on the traffic flow. At the same time in many countries, ISPs were agreeing to lift or entirely cancel the data caps on last-mile consumer internet connections, which definitely is something we haven’t seen before.
We were also interested to see if, and how, the number of IX participants changed. To take a step into that direction, we used the PacketClearingHouse data: https://www.pch.net/resources/.
Although, evidently, PCH does not have 100% coverage of all the world's Internet Exchange Points, the amount of information it gets from the major ones is sufficient for this kind of experiment. We have seen individual IXes to offer free memberships and connections, so we wanted to look if the situation is similar worldwide and if participation in traffic exchange was motivated by the pandemic.
In short — no, the number hasn’t generally changed.
The tremendous growth of traffic on major Internet Exchanges
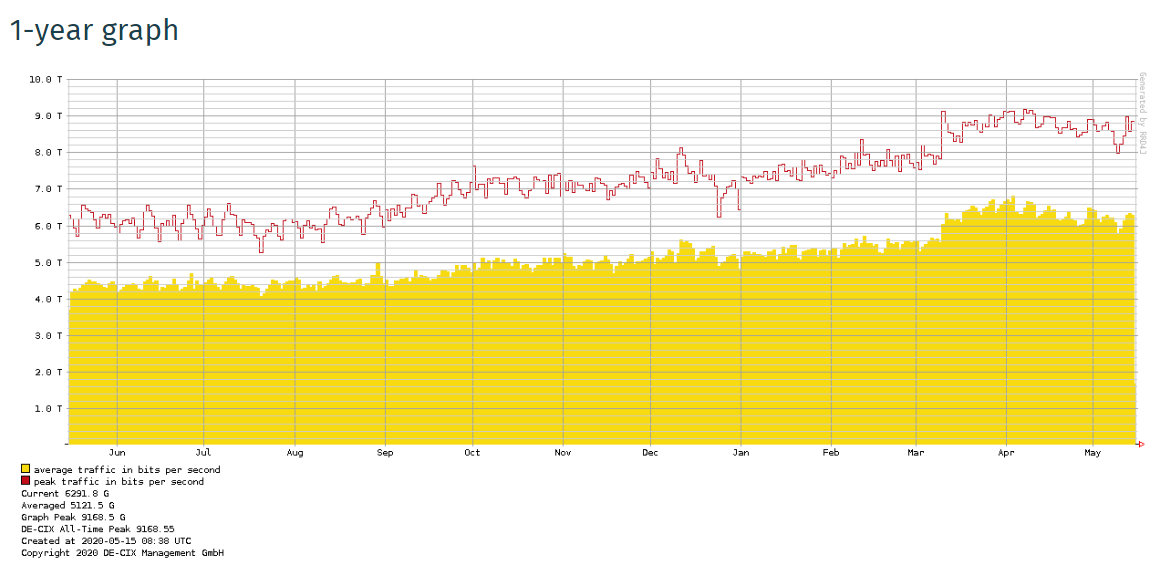
DE-CIX
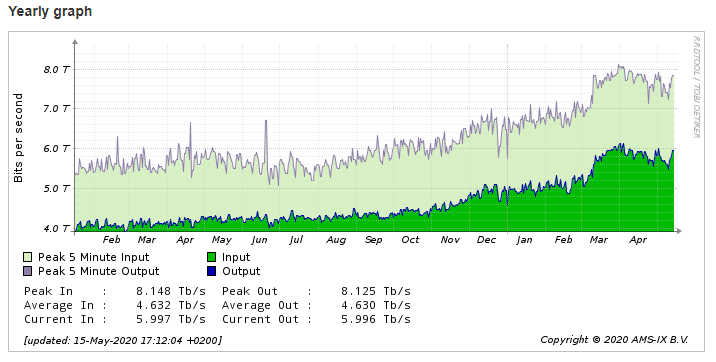
AMS-IX
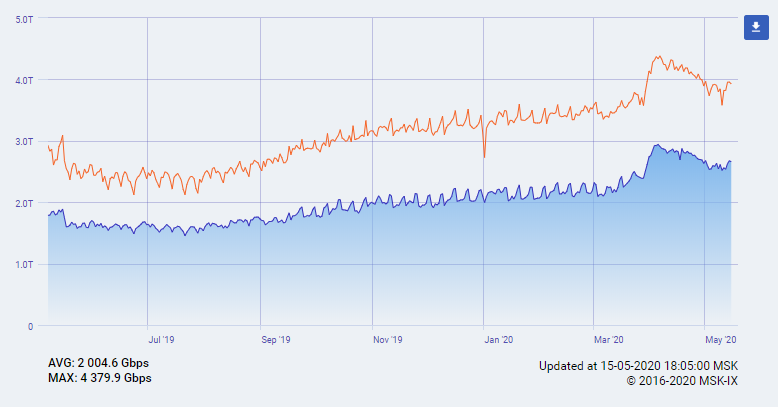
MSK-IX
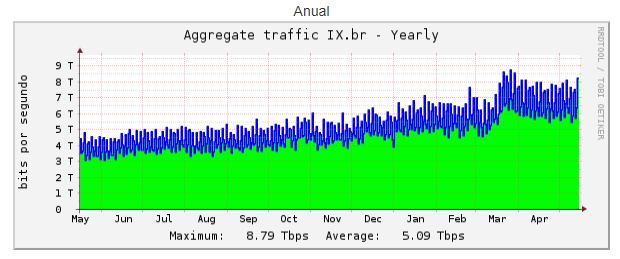
BR-IX
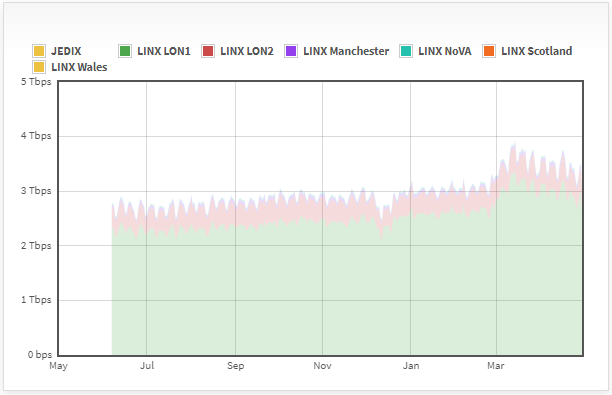
LINX
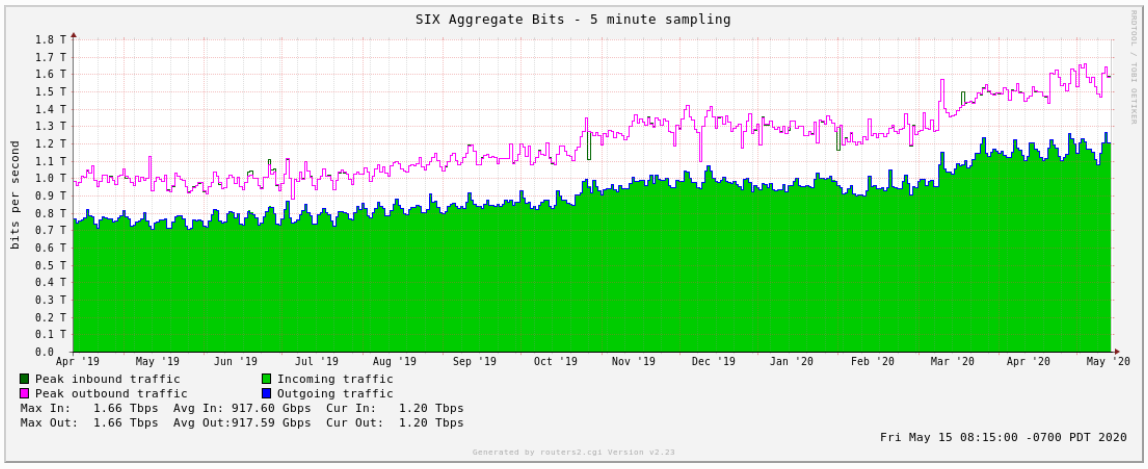
SI-X
You could compare all those graphs from the largest IXes in the world with the graphic of our own, illustrating overall traffic growth within Qrator Labs filtering network from January 28 till May 1.
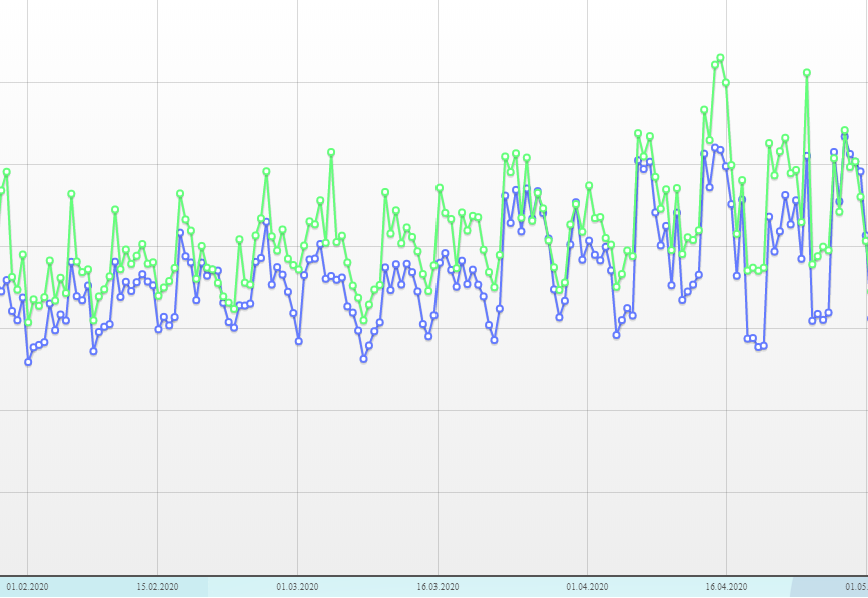
Qrator Labs overall traffic dynamics from 28.1.2020 to 2.5.2020
As you can see, it was truly a worldwide pandemic and this time we had the Internet.
We won't paste the participants' graphics here as there are lots of them. For the sake of saving space and volume of this article, we would like to write it with our own words simply — there is no correlation between the traffic growth on Internet exchange points and the number of participants on those exchanges. To put it merely — traffic spiked everywhere, for each and every transit network.
Routing incidents during three months
During the period in question, we reported 6 significant routing incidents at the Radar blog. Those were events where severity and propagation combined to a significant extent, making those incidents visible outside of one particular region. And the one that happened on April 24 was as odd as the time we're living in — it contained only valid routes with correct ROA objects, and it did spread, although not wrecking as much havoc, yet. It was two days after we once again saw what we suppose to be a BGP optimizing software playing with networks from inside. Curious indeed.
If we want to take a look at the monthly statistics of routing leaks from the beginning of the year, it would look like that (we’re only taking into consideration leaks with significant distribution):
January: 1
February: 4
March: 6
April: 6 +1 in IPv6
So there is a growing trend on routing incidents we just don’t know yet how long it would last. Also, it is important to notice that since most routing incidents happen due to misconfiguration errors, the biggest threat is the moment everybody comes back to their offices and starts making changes to adapt to changed realities.
National Internet Segments Reliability Changes
We are 4 months before the release of our annual National Internet Segments Reliability Report. If you don’t know what that is — take a look at the 2019 version.
We want to outline a little teaser about how the global reliability changed during those three months with short bullet points that we would elaborate on in the comprehensive research in August, as usual.
- Brazil and Argentina significantly improved their positions in the top-20 of most reliable internet segments;
- Japan and the United States also showed an overall rating growth, although not that significant as the two South American countries;
- Maybe this is due to the fact that Level3 is still the most important Autonomous System in the United States. At the same time, the critical ASes in the other three countries: Brazil, Argentina and Japan, changed in comparison to 2019.
It is also interesting to add, that according to the same IX statistics and some additional data, like Google statistics, we could say that the pandemic slightly sped up the IPv6 adoption — a fact The Register also noticed at the end of March.
—
Recommendations:
http://instituut.net/~job/netops_during_pandemics.pdf — slides by Job Snijders from NTT with recommendations for network operation during pandemics;
https://www.sans.org/security-awareness-training/sans-security-awareness-work-home-deployment-kit — SANS Security Awareness Work-from-Home Deployment Kit;
