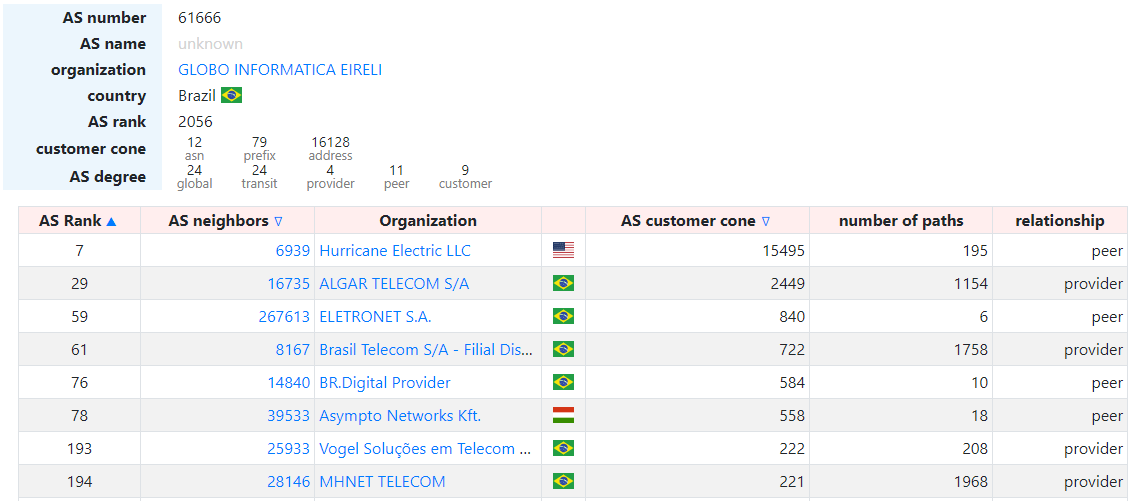
January 27 of the year 2021 was marked with quite a peculiar route leak. AS61666 - GLOBO started announcing prefixes of its upstream provider MHNET - AS28146 to its another provider ALGAR - AS16735. In three minutes GLOBO leaked 1330 prefixes, and the whole routing incident lasted for 8 minutes - a time that was enough to create 1435 conflicts in 21 countries with 265 ASNs, mainly in Brazil (194 ASNs), United States (22 ASNs) and Venezuela (7 ASNs).
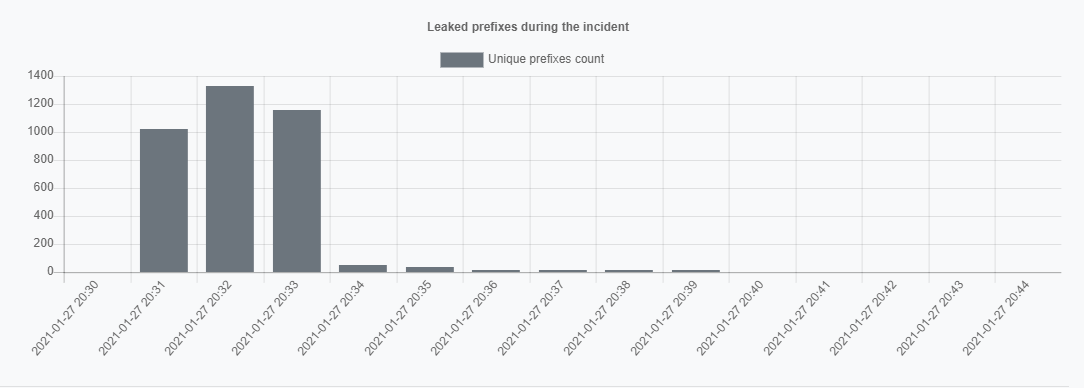
This incident distributed among 86% of BGP speakers at its peak, which is a significant percentage. Almost 10% of the prefixes in leak had Invalid ROA (154 prefixes) and did not help prevent the spreading.

But what is even more impressive with this route leak is that these paths had a HUGE prepend within their AS_PATH attribute - 16(!).
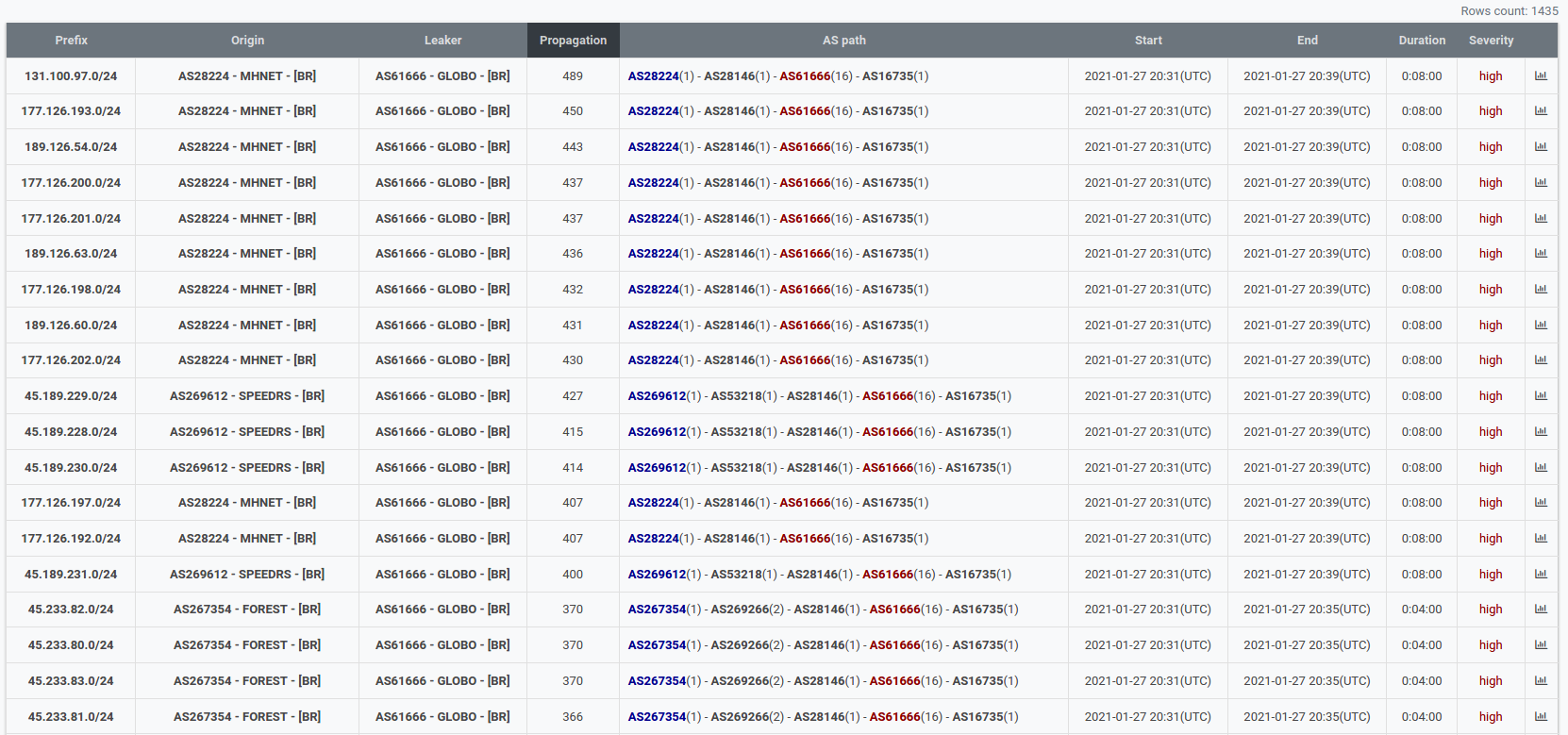
In a normal situation, prefixes with such heavily prepended AS_PATHs distribute poorly, as usually a more lightweight and shorter alternative route could be found and, eventually, taken as the best. However, in this leak, we see a lot of prepended AS_PATHs that managed to distribute globally. How did that happen?
The shorter route won’t win the path challenge if there’s no such route. In this case, the distribution was better on leaked routes only for those prefixes that before the incident weren’t globally distributed (indicating local use).
It turns out that almost all such prefixes, beforehand, were covered by less specific prefixes - meaning that the local /24 leaked in the incident was covered by a globally distributed /23 before the incident. If there existed any service inside those networks - before the leak, they were available through the less specific and regular routes. After (and during) the incident more specific prefixes with humongous prepends broke out and started distributing, therefore taking all the traffic through the leaked link.
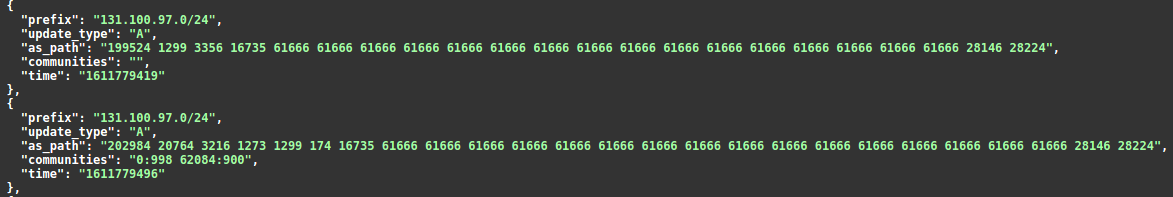
So in this particular case, even tremendous prepend wasn’t a problem for the leaked prefixes global distribution because of their prior local use.