
Let's take a deeper look at the Q1 2023 DDoS attacks mitigation statistics and observations from Qrator Labs' perspective.
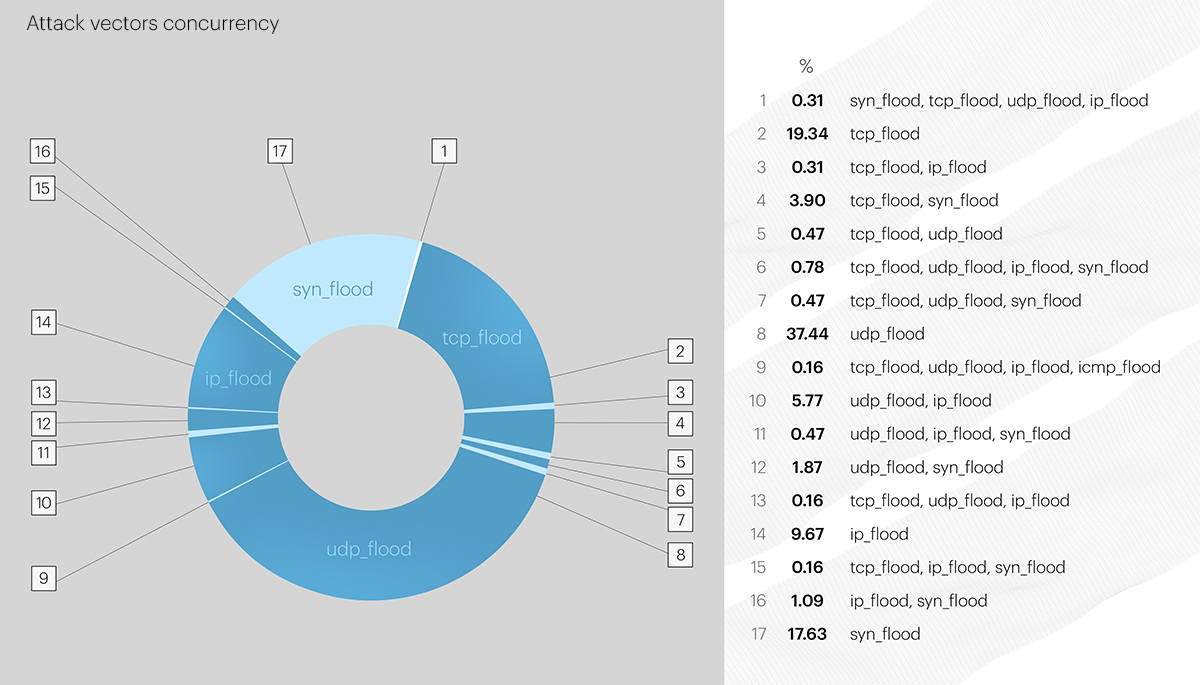
In the first quarter of 2023, the following attack vectors were prevalent:
- UDP flood, with 37.44% percent of all L3-L4 attacks;
- TCP flood, with 19.34% of volumetric attacks;
- And SYN flood, with a 17.63% share.
The UDP flood has reigned among all the attacking vectors for a year. But the second and third places are being taken by different vectors based on the changes in techniques attackers exploit. In Q1 2023, TCP flood again gained momentum and was responsible for almost 20% of all mitigated attacks, with SYN flood dropping only slightly compared to Q4 2022 - from 26.84% to 19.34% this last quarter.
These top-3 vectors combined make 74.41% of all the mitigated volumetric attacks of Q1 2023 - 3.28% less than in Q4 2022.
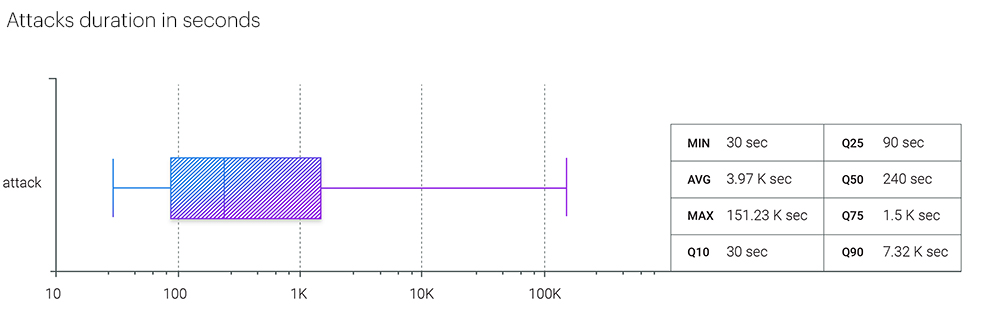
In Q1 2023, attacks grew longer from almost every perspective. Average attack time grew significantly QoQ, from 2503 seconds in Q4 to 3970 seconds in Q1 2023. The median went up as well - from 210 seconds to 240 seconds.
But there was no record attack duration in Q1 2023; the longest attack lasted for 151 230 seconds, approximately 42 hours. In Q4 2022, the value was at 69 hours, and in the first quarter of 2022, we found one attack that persisted for 11 days.
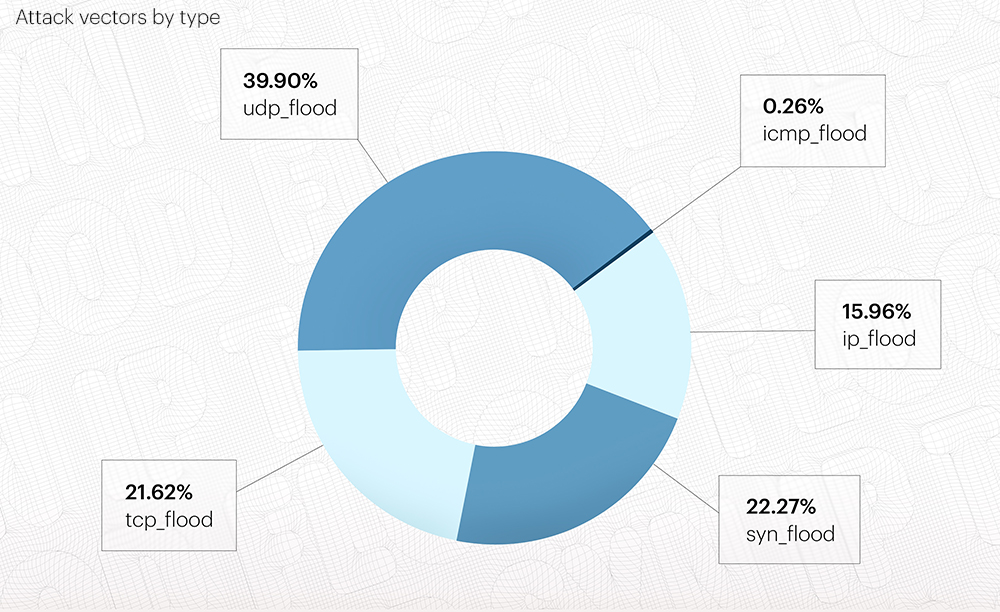
In the attack vector statistics without concurrency, we can see what vector gained the most QoQ - this time, it's UDP flood, which amassed 39,9% in Q1 2023.
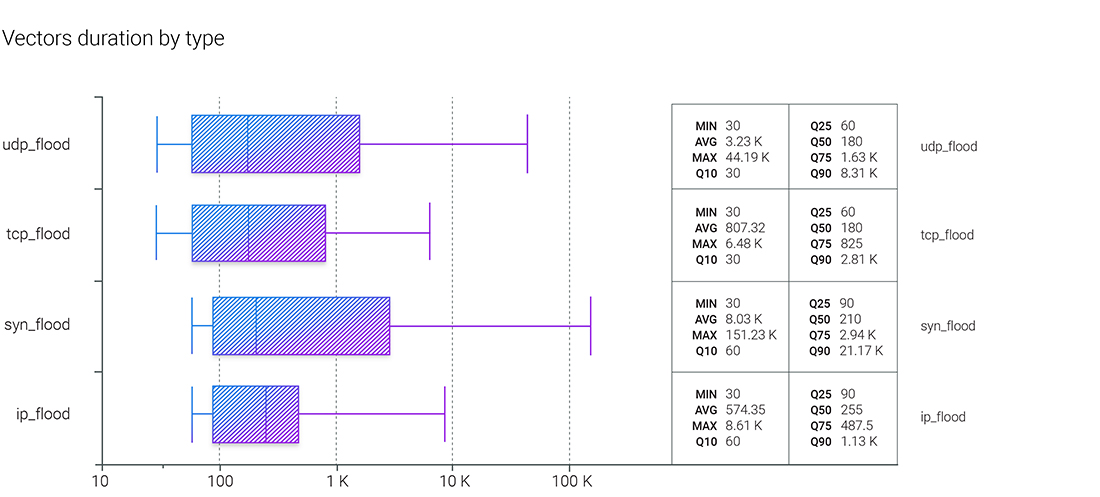
This picture is becoming more or less standard: the SYN flood with the longest duration, followed by the UDP flood and then the IP flood, with the latter two sometimes swapping forms.
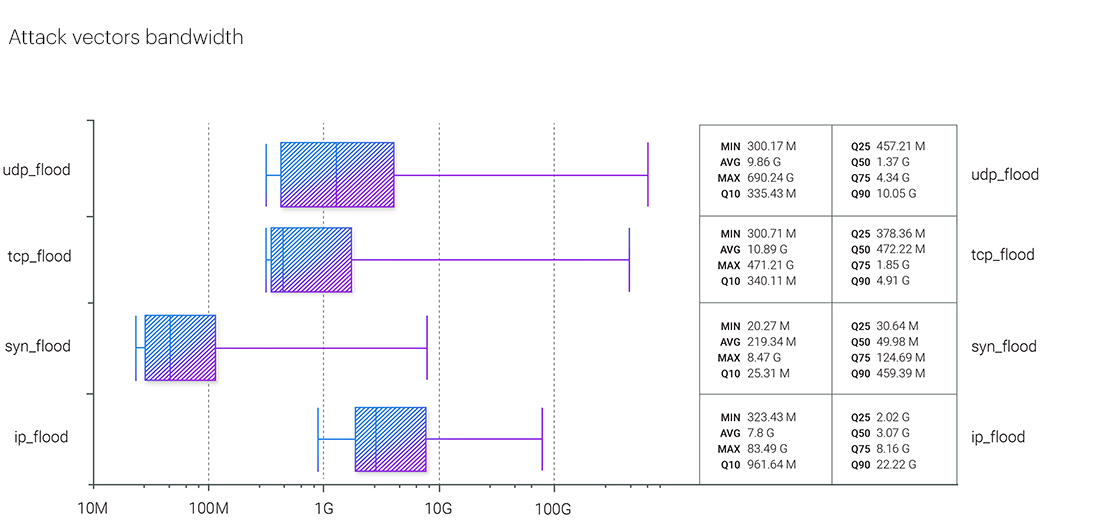
Same as Q4 2022, UDP flood and TCP flood have higher maximums - 690.23 Gbps and 471.21 Gbps respectively. That is also true for the median, which behaves exactly like the previous quarter - this time, the UDP flood shows 1.37 Gbps, which is still more than two times lower than the IP flood median bandwidth of 3.07 Gbps.
The trend turned for the Q10 to Q90 range in UDP flood, which was shrinking for all of 2022, but now we see that UDP floods become much more diverse in their bandwidth.
In the quarterly reports, we register the development of the average (L3 - L4) attack bandwidth from quarter to quarter. In the last quarter - Q4 2022 - the absolute average was 9.736 Gbps - the record average bandwidth in 2022, slightly less than the highest average bandwidth in the past - 9.15 Gbps in Q1 2021.
In Q1 2023, the average attack bandwidth was 7.59 Gbps Gbps - probably the lowest during the lifetime of our observation. These values only apply to volumetric attacks.
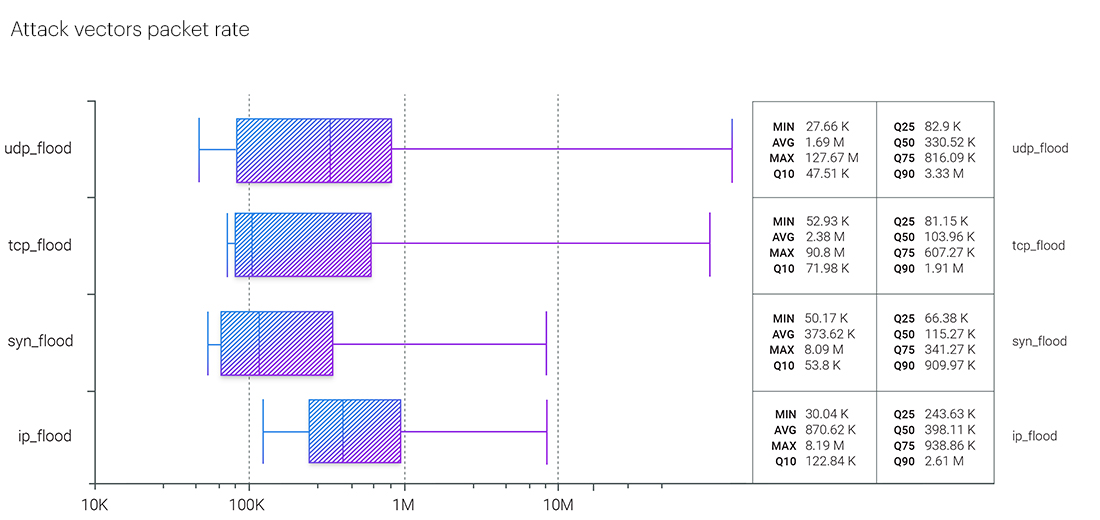
Things have also changed in the packet rate performance of different vectors. Unlike the previous quarter, in Q1 2023, TCP flood no longer demonstrated the most significant median value - that time, it was IP flood. However, the maximum was still in the UDP flood's basket with an attack of 127.67 MPPS.
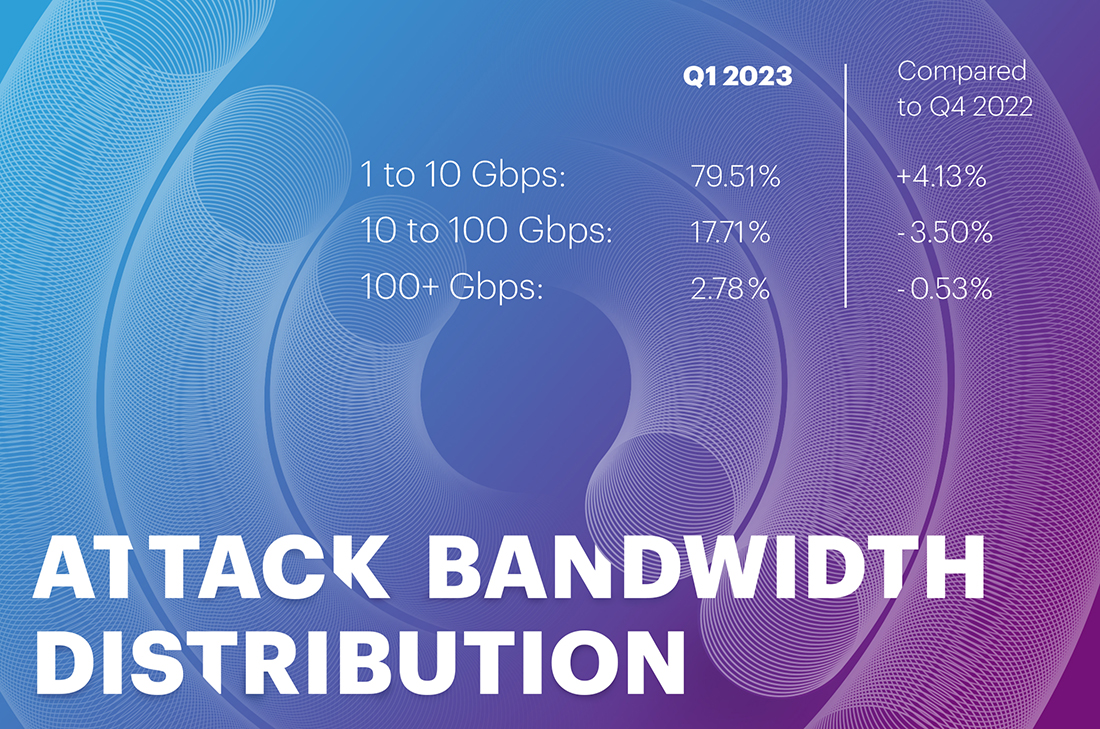
In Q1 2023, all the bandwidth ranges lost to the smallest one - 1 to 10 Gbps - where we can now find almost 80% of all volumetric attacks.

Again, in Q1 2023, there were no big fish regarding attack sources, networks, botnets, etc. The most significant attack source we observed contained 131 628 devices - almost the same as in Q3 2022.
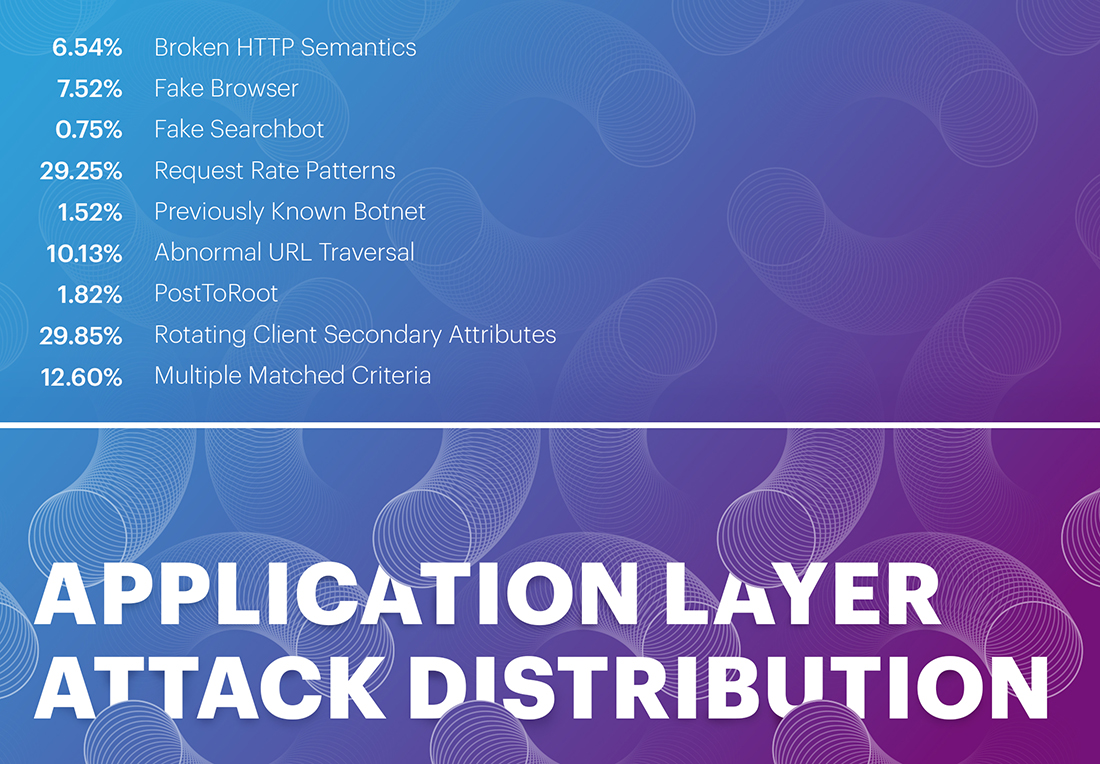
Q1 2023 was the seventh quarter in which we attempted to categorize the application layer, or L7, DDoS attacks.
The largest category in Q1 2023 was Rotating Client Secondary Attributes, which refers to an unusual set of headers in the request, and accounts for more than a quarter - 29.85% - of L7 DDoS attacks.
Request Rate Patterns followed second, which includes anything that deviates from what is expected from a legitimate user regarding request rate, and collected 29.25% of Q1 2023 application layer attacks.
That differs from the third category, Abnormal URL Traversal, which is exactly what it sounds like - an action that a legitimate user often wouldn't even be able to perform, where we saw 10.13% of the attack data.
Broken HTTP semantics now accounts for "only" 6.54% of L7 attacks.
The top four categories together account for 75.77% of L7 attacks, with 12.60% in Multiple Matched Criteria, where we put all concurrent L7 attacks.

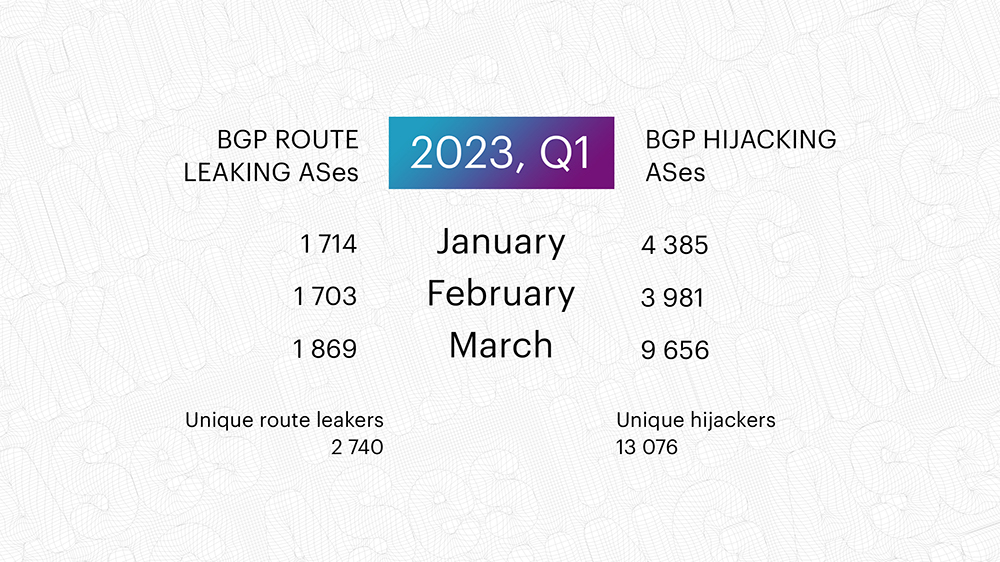
Looking at the number of unique BGP route leakers and unique BGP hijackers, it would appear that nothing is happening - which is far from the truth. The number of unique route leaking ASes remains roughly the same as in Q4 2022, but the number of unique hijacking ASes has increased by almost 30%.
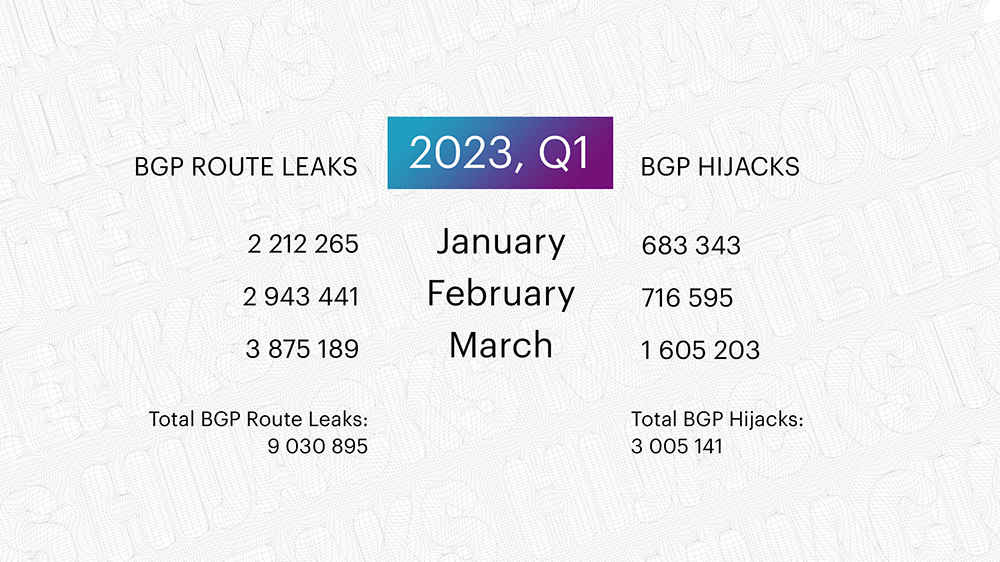
Remember, here, we are counting the total value and not the unique routing incidents - if one AS originates a route leak, that is distinguished as a separate one by the Qrator.Radar model - we count it in.
In Q1 2023, Qrator.Radar recorded 9 030 895 individual BGP route leaks - three times more than in the previous quarter. And the number of hijacks grew significantly - Q1's 3 005 141 are eight hundred thousand more than in Q4 2022
Let us look at the global incidents that are part of these statistics for each quarter month.
Reminder: The Qrator.Radar team has a set of certain thresholds that separate global incidents from the rest. These include affected prefixes, affected autonomous systems and the distribution of the incident across routing tables.
Global BGP Route Leaks in Q1 2023:
- January: 5
- February: 4
- March: 0
A detailed description of these incidents by date of occurrence can be found on the Qrator.Radar Twitter feed.
Global BGP Hijacks in Q1 2023:
- January: 0
- February: 1
- March: 1
Bot Protection Statistics, Q1 2023
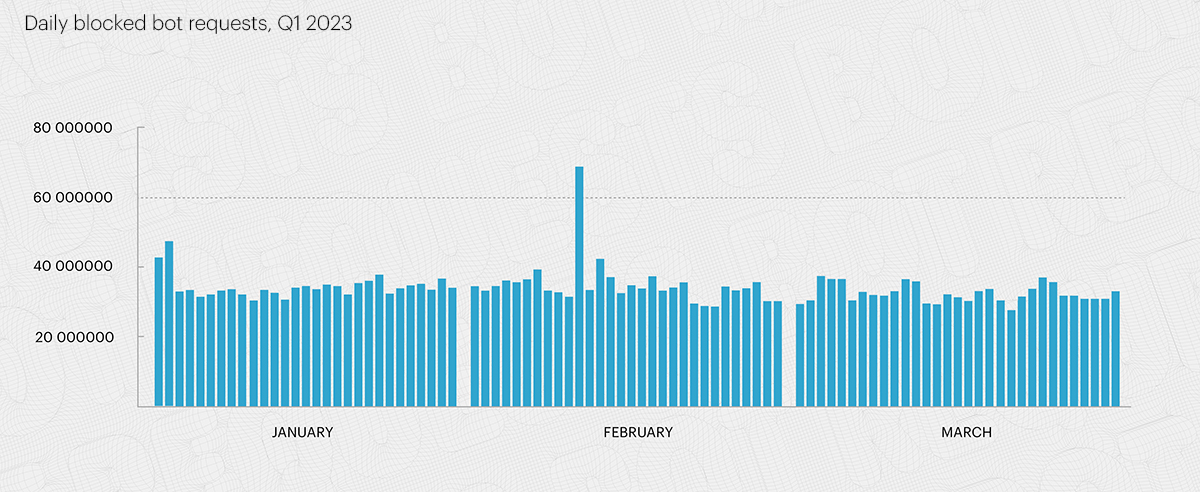
Qrator Labs has been working on a new technology called Bot Protection for a few years now. That is the second time we have looked at the statistics of bad bot protection and summarized the newly acquired data for Q1 2023.
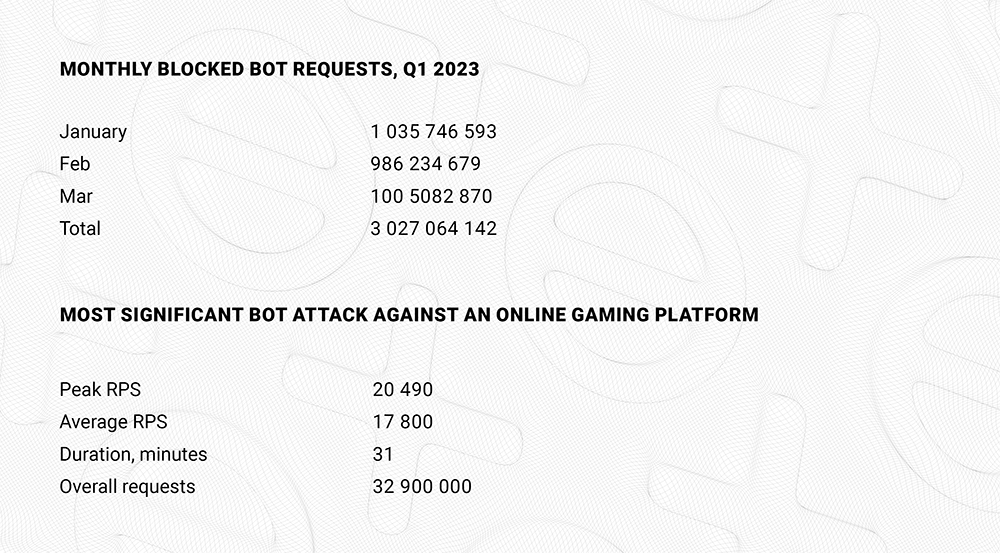
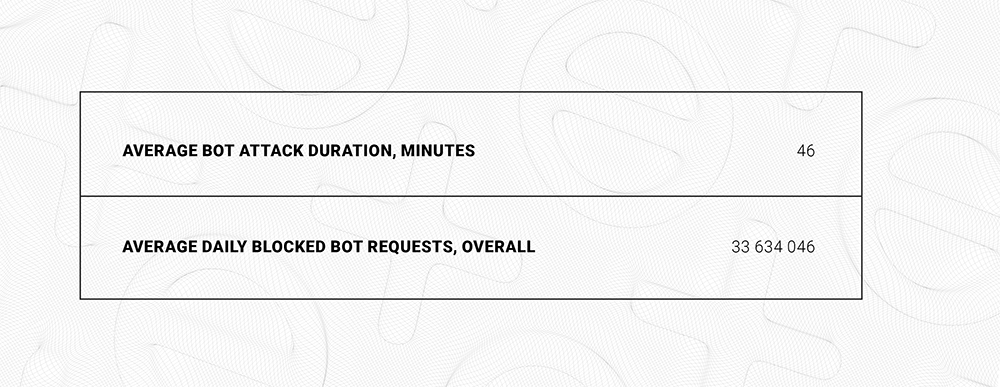
As you can see, the number of bad bot attacks is relatively high - measured in billions of requests - even though Qrator Labs has only recently started offering this product to its customers.
The most significant attack occurred on February 2, when an online gaming platform was attacked for 31 minutes with an average RPS of 17 800, peaking at 20 490 RPS.
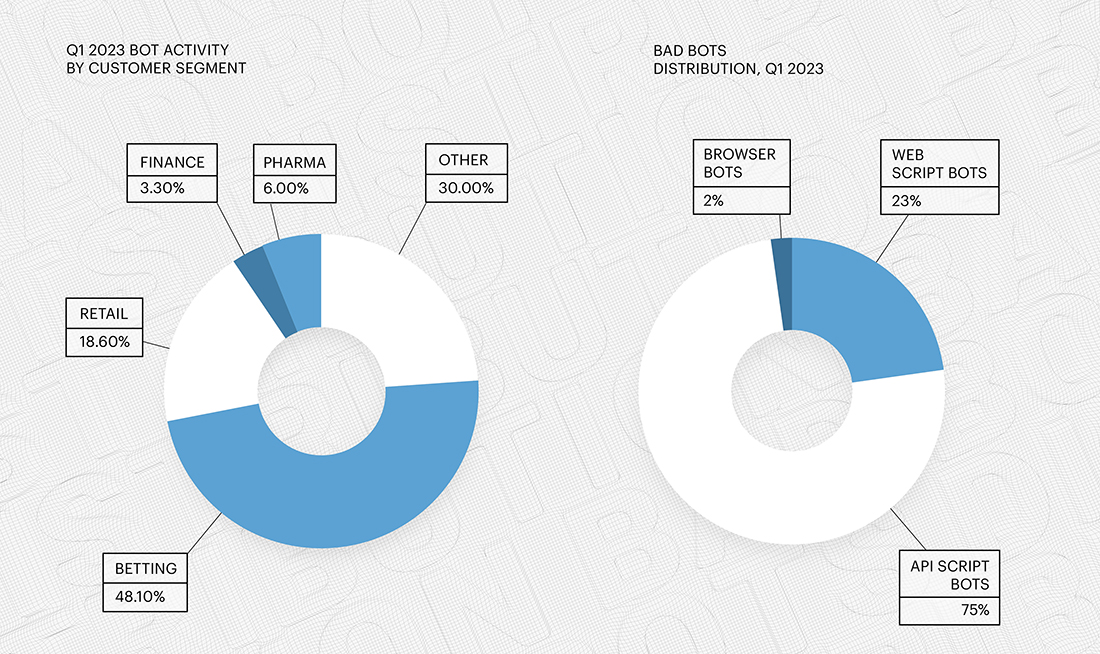
As you can see, there are more and less exposed industries when it comes to automated bot attacks. Betting and retail are the most affected, followed by finance and pharmaceuticals. The bot distribution in Q1 2023 changed significantly compared to Q4 2022 - now API Script Bots represent a ¾ of all malicious bot activity.
In compiling this data, we thought that the most exciting part of the bot attack statistics was the overall "background" level of bad bot attack noise. Most actively parsed targets on the Internet are parsed daily, either in bursts or slowly, but 24/7. That is what makes money for the people who develop and run them, as scraping, scalping, brute forcing, and other techniques remain in a niche of their own.
Thank you for reading the Qrator Labs Q1 2023 Report!
Data sources and observation methodology
Qrator Labs' Quarterly and Annual Reports are based on the data from observed attacks on web pages and servers under the Qrator Labs' DDoS attacks mitigation service and customers' insights on the mitigated attacks. The figures and data were collected according to the report's timeframe scope, i.e., a specific calendar quarter or calendar year.
Each report consists only of the attack data Qrator Labs directly observed ("mitigated"). Qrator Labs does not collect or analyze traffic outside of its network, meaning that all the conclusions we draw are based solely on the data passing through the Qrator BGP anycast network. By 2023 Qrator Labs' anycast network exceeded 3 Tbps of filtering capacity built upon 15 points-of-presence, each connected to a Tier-1 ISP.
Qrator.Radar analyzes BGP paths data collected from more than 800 sessions, providing analytics and real-time incident monitoring to the registered and authenticated owners of Autonomous Systems. Qrator.Radar provides a user with historical data on AS connectivity (links), BGP routing anomalies, and network-related security issues.
Qrator.Radar is the BGP monitoring and analytics tool and the vulnerability scanner for known networks.
That means that when scanning a network, Qrator.Radar analyzes the presence of any known amplificators and the amplification (https://en.wikipedia.org/wiki/Denial-of-service_attack#Amplification) factor itself. This data is further processed to give ISP (or, more precisely, ASN) owners the possibility to analyze the availability of any of those services which attackers could exploit for DDoS attacks.
Such scans are not harmful in any way to the company's hardware or software, Qrator.Radar collects the data only to notify the rightful owners of the network of when and which amplificators became available within the networks they manage. We require authorization from the ASN owners before showing this kind of information we consider sensitive.
Besides the network data and its analysis, Qrator Labs also employs open-source intelligence analysis within the public reports. Qrator.Radar, in turn, uses data from publicly available databases to get the IRR, RPKI and geolocation information to correlate between its own and open-sourced data.
