A distributed denial of service (DDoS) attack is a malicious attempt to disrupt the normal functioning of a targeted server, service, or network by overwhelming it with a flood of internet traffic. The attacker sends a high volume of requests to the target, consuming its resources such as bandwidth, memory, and processing power.
As a result, the targeted system becomes unresponsive or crashes, preventing legitimate users from accessing the service. DDoS attacks can cause significant financial losses and reputational damage to organizations by rendering their online services unavailable.
However, not all DDoS attacks are identical. While the ultimate goal is to exhaust a server or site's resources to the point where legitimate users are denied access, the methods used to achieve this can vary. This variation in approach affects how difficult each type of attack is to mitigate. In this article, we're going to explore layer 4 (transport layer) and layer 7 (application layer) DDoS attacks.
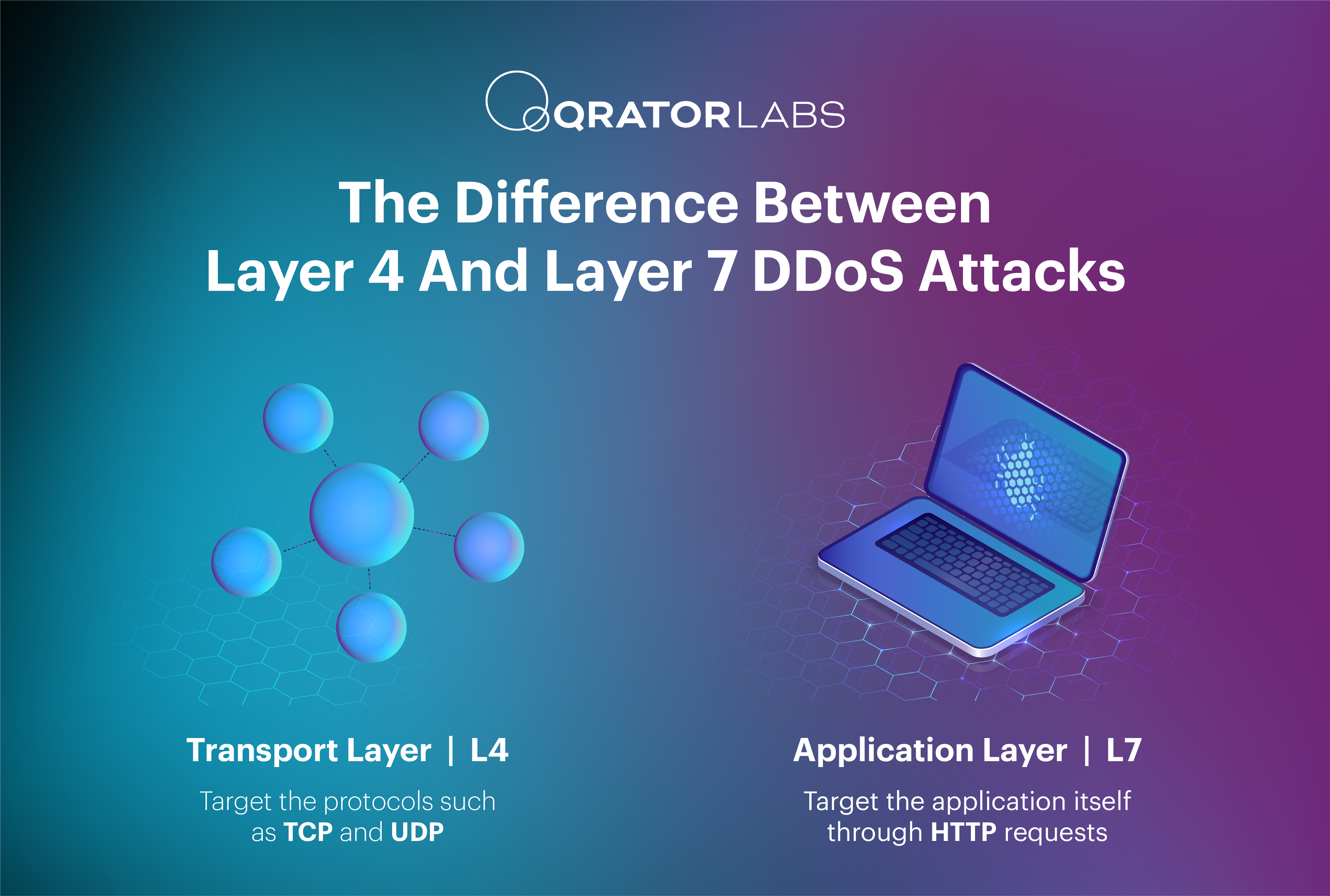
Layer 4 DDoS Attacks
Layer 4 DDoS attacks, also known as transport layer attacks, target the transport layer of the OSI model, which includes protocols such as TCP (transmission control protocol) and UDP (user datagram protocol). These attacks aim to overwhelm the network infrastructure by exploiting the protocol behavior.
One common type of layer 4 attack is the SYN flood. In this attack, an attacker sends a barrage of SYN requests to the target server. The server responds with SYN-ACK packets, but the attacker never completes the handshake by sending back an ACK. This leaves the server with numerous half-open connections, eventually exhausting its resources and causing it to become unresponsive.
UDP floods are another example of layer 4 attacks. In a UDP flood, the attacker sends a large number of UDP packets to random ports on the target server. The server, unable to find the application associated with these ports, responds with ICMP destination unreachable packets. The sheer volume of these responses can overwhelm the server and its network infrastructure.
Layer 7 DDoS Attacks
Layer 7 DDoS attacks, also known as application layer attacks, operate at the application layer of the OSI model. These attacks target the application itself rather than the network infrastructure, making them more sophisticated and harder to detect.
HTTP floods are a common form of layer 7 attacks. In an HTTP flood, the attacker sends a high volume of HTTP requests to the target server, typically requesting resource-intensive operations such as database queries or large file downloads. This can quickly exhaust the server’s CPU and memory, leading to a denial of service for legitimate users.
Another example of a layer 7 attack is the slowloris attack. Slowloris works by opening multiple connections to the target server and sending partial HTTP requests. The attacker keeps these connections open by periodically sending additional HTTP headers, never completing the requests. This ties up server resources, eventually leading to a denial of service.
Cybercrime Activity
DDoS attacks are often commoditized through services known as "booters" or "stresser services." These platforms allow individuals to launch DDoS attacks with minimal technical knowledge, simply by paying a fee.
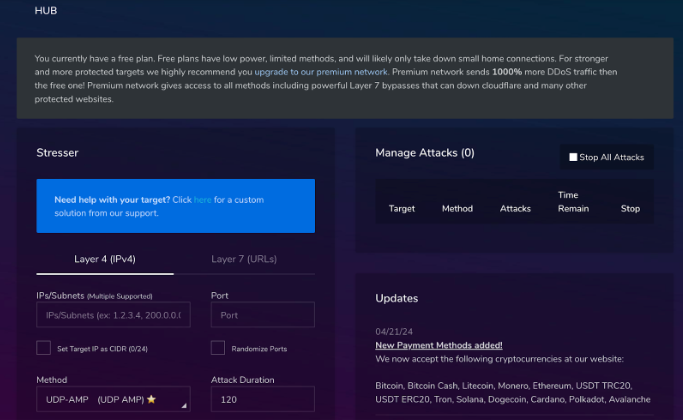
Booters typically offer a variety of attack types, catering to both layer 4 and layer 7 attacks. For instance, a booter might advertise the ability to launch SYN floods, UDP floods, and other layer 4 attacks, alongside HTTP floods and slowloris attacks for layer 7. The choice of attack often depends on the target and the desired impact.
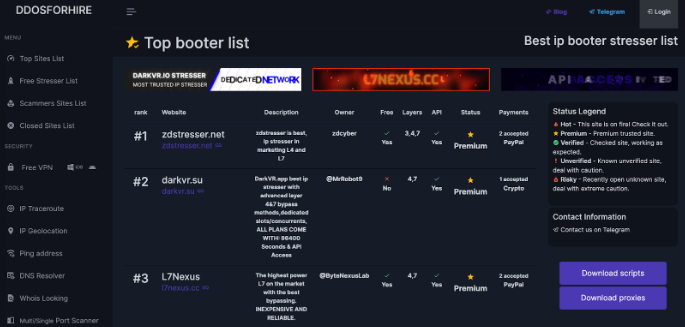
On cybercrime forums, discussions around booters are common. Users share reviews of different services, discuss tactics for bypassing security measures, and exchange tips on optimizing attack strategies. The availability of such services has democratized the ability to launch DDoS attacks, leading to an increase in frequency.
Attack Examples
The history of cybercrime is replete with stories of high-profile DDoS attacks.
One notable example is the 2012 attack on U.S. financial institutions, known as Operation Ababil. This campaign, attributed to a group called the Izz ad-Din al-Qassam Cyber Fighters, primarily used layer 7 attacks to disrupt online banking services. The attackers leveraged HTTP floods to overwhelm the web servers of major banks, causing significant downtime and financial losses.
Another infamous example is the 2016 Dyn attack. This attack targeted Dyn, a major DNS provider, and caused widespread internet outages. The attackers employed a massive botnet composed of IoT devices infected with the Mirai malware. While primarily a layer 3/4 attack, the sheer scale of the traffic generated had ripple effects that impacted services at the application layer as well.
Protection Against DDoS Attacks With Qrator.AntiDDoS
Protect your operations from malicious DDoS attacks with Qrator’s leading anti-DDoS solution. We offer comprehensive protection against all types of DDoS threats at every layer of the OSI model.
Our geo-distributed filtering network, with over 4 Tbps of network bandwidth, ensures your applications stay online and perform optimally even during large volumetric attacks. Our service mitigates sophisticated multi-vector attacks across all protocol layers, guaranteeing 99.95% uptime through SLA.
Rest easy knowing that Qrator’s multi-layered DDoS defense protects your business. Contact our sales team today to learn more about securing your online presence and protecting your business from DDoS attacks.
