Recent years have seen distributed denial-of-service (DDoS) attacks grow larger and happen more often than ever before. In just the first three months of 2025, the number of DDoS attacks worldwide increased by 110% compared to the same period the year before.
One late-March incident involved a botnet of 1.33 million compromised devices, almost six times larger than the biggest botnet observed the year prior. That botnet blitzed an online betting platform, and over half of the attacking devices originated from a single country (Brazil). In the following quarter, its size grew to 4.6 million devices, and by the next quarter, it reached 5.76 million.
Internet-of-things (IoT) devices have emerged as a driving force behind many of these massive attacks. The majority of bots in today’s DDoS swarms are everyday IoT products, such as Wi-Fi routers, TV boxes, IP cameras, and digital video recorders.
With tens of billions of IoT devices now online, attackers have an enormous pool of poorly secured mini-computers to enlist. In effect, IoT gadgets have become the hidden amplifiers of DDoS mayhem, quietly hijacked in bulk to fire hose targets with malicious traffic.
Why IoT devices are especially vulnerable
IoT devices often make easy prey for attackers due to a confluence of security shortcomings.
For one, many come with weak default credentials, usernames and passwords that are well-known, guessable, or even hardcoded into the device firmware. It’s common for consumers to plug in a new camera or router and never change the default admin login. Attackers capitalize on this by automating scans for devices still using factory credentials.
The OWASP IoT Top 10 list actually ranks hardcoded passwords as the number-one vulnerability in IoT, followed closely by insecure network services exposed on these devices. Many IoT products run lightweight web interfaces or old protocols (Telnet, UPnP, etc.) that lack encryption and authentication. These unnecessary services dramatically expand the attack surface, often listening openly on the internet for any would-be intruder.

Another big issue is the lack of regular updates and patches. IoT vendors frequently treat devices as ship-and-forget, leaving even serious software vulnerabilities unpatched forever. Users rarely get prompted (or bother) to update their router or IP camera firmware. Over time, vulnerabilities accumulate. A device that shipped in 2018 might still be running that same firmware in 2025, along with all its known vulnerabilities.
Finally, limited built-in security features exacerbate the problem. A lot of IoT devices lack mechanisms like host firewalls, intrusion detection, or access controls. They are essentially plug-and-play on the open internet, prioritizing ease of use over security.
Global regulations and best practices strengthening IoT security
The recognition of IoT’s security risks has prompted responses on several fronts. Industry standards and government regulations are beginning to enforce basic security hygiene for IoT products.
California implemented a pioneering IoT security law (SB-327) in 2020 that bans default credentials on any internet-connected device sold in the state. The law mandates that each device must either come with a unique password or force the user to set a custom password upon first use — effectively outlawing the ubiquitous “admin/admin” logins that Mirai and similar malware abused.
Likewise, the United Kingdom’s new Product Security and Telecommunications Infrastructure (PSTI) Act (effective April 2024) shifts responsibility to manufacturers to build in security by design. The UK regulations require three key measures:
1. IoT product makers must clearly disclose how long they will provide security updates/support for each device.
2. No universal default passwords, every device must have a unique password or require a user-defined password at setup.
3. Manufacturers must establish a vulnerability disclosure policy so that security flaws can be reported and fixed promptly.
These rules directly address the most common issues by ensuring devices aren’t deployed with known-bad defaults and by encouraging a lifecycle approach to IoT security, including ongoing updates and patch management.
Yet even with these measures, the market reality complicates things. Security features increase costs, while many budget-friendly devices are sold with little to no long-term support. Most consumers prioritize price over security, which allows devices to remain in circulation and limits the overall impact of regulation.
Beyond laws, there are industry best practices and technical standards aimed at fortifying IoT devices. Manufacturers are applying measures like secure boot and firmware signing to harden devices against tampering. Secure boot means the device will only run firmware that has been cryptographically signed by the vendor, preventing attackers from simply uploading their own malware-laden firmware.
Likewise, signing OTA (over-the-air) updates ensures that devices reject any unauthorized or malicious firmware updates. Newer best practices also include features like encrypted communication by default (so that data and commands to the device can’t be intercepted or altered) and automatic update mechanisms with user notification.
Industry groups such as the IoT Security Foundation and standards bodies like NIST and ENISA have published detailed guidelines to help manufacturers implement these features.
NIST, for instance, has a guideline listing simple security capabilities consumers should expect, things like unique device identifiers, secure default settings, the ability to change passwords, to update firmware securely, and event logging for security incidents.
How cybercriminals exploit IoT vulnerabilities to build DDoS botnets
On the flip side of these defensive efforts, threat actors are busily weaponizing vulnerable IoT devices. In cybercrime communities, IoT exploits and access are bought and sold like commodities. The screenshot below shows an example of a forum advertisement where a seller is offering pre-hacked IoT devices for $0.50 apiece.
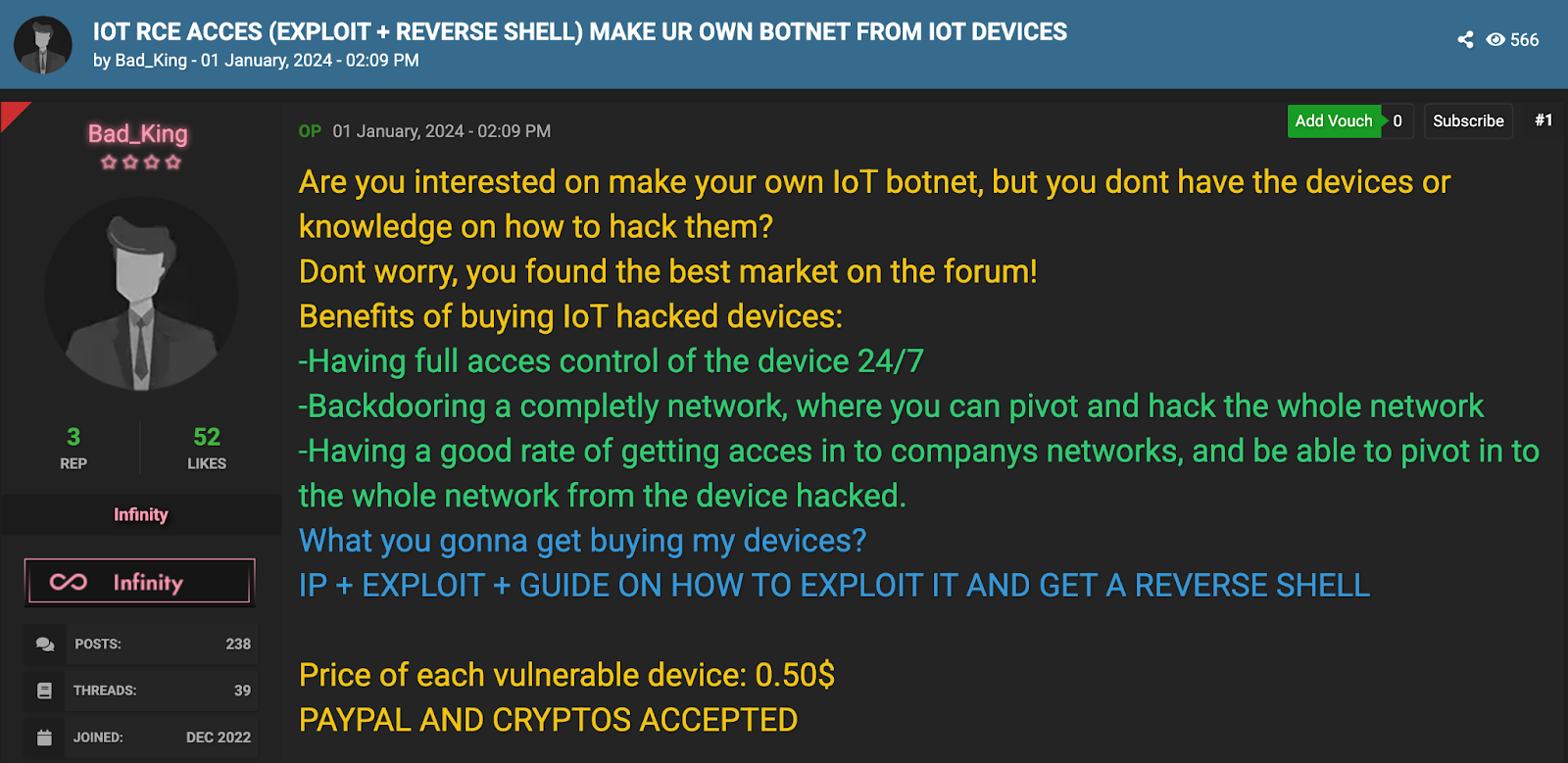
In this marketplace post, the seller promises full access to the device 24/7 and even provides the IP address, the exploit needed, and a step-by-step guide on obtaining a reverse shell (remote command access) on each device. The pitch shows that by purchasing these hacked IoT nodes, a buyer could backdoor entire networks — using an infected camera or router as a foothold to pivot deeper into a victim’s network.
In essence, services like these hand over ready-to-use IoT bots complete with RCE (remote code execution) exploits, lowering the skill barrier for criminals to assemble their own botnets. With a few dollars, an attacker can acquire dozens of IoT machines, each quietly under their control and poised to participate in DDoS attacks or other malicious campaigns.
In addition to selling access, cybercriminals also distribute scanning tools to optimize the process of finding new vulnerable IoT targets. The second image is a forum post advertising an “IoT Scanner” utility. This tool boasts features like automatically identifying open IP cameras, routers, and other IoT endpoints, multi-threaded scanning for high speed, and support for wide ranges of IP addresses, even generating random targets to scan continuously.

In practice, these scanners allow attackers to crawl the internet for exposed devices on a massive scale — for example, sweeping for webcams that still use their default passwords or routers with unpatched firmware bugs. Once the tool finds a susceptible device, the attacker can attempt a known exploit or default login to gain control, often installing lightweight malware or opening a reverse shell to the device.
Compromised IoT devices are then herded into botnets, where they await commands from a controller. When directed, they can launch floods of traffic — such as UDP packets or HTTP requests — at chosen victims as part of a DDoS attack.
How Qrator Labs protects networks from IoT-powered DDoS botnets
While new IoT products are becoming more secure, millions of older and poorly protected devices remain online and continue to be pulled into botnets. Tackling this issue takes more than basic defenses — it requires research and protection that track how these attacks evolve.
At Qrator Labs, we study DDoS trends in depth, from how botnets are built to the techniques they use, and we fold that knowledge directly into our mitigation services. For teams defending networks or investigating attacks, our reports and expertise can make a difference.
With the right intelligence and proactive defenses, it is possible to keep pace with the surge of IoT powered DDoS and blunt the impact of attackers hijacking everything from routers to IP cameras. For more on IoT embedded DDoS attacks and ways to strengthen defenses, see Qrator Labs’ latest resources and solutions.
