One would expect 2021 to start somewhat differently compared with chaos of the previous year. In Qrator.Radar, we also hoped for the better. Unfortunately, as soon as January 6 - today, we proved wrong.
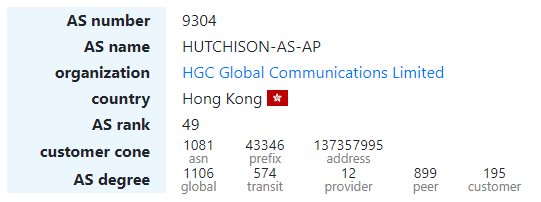
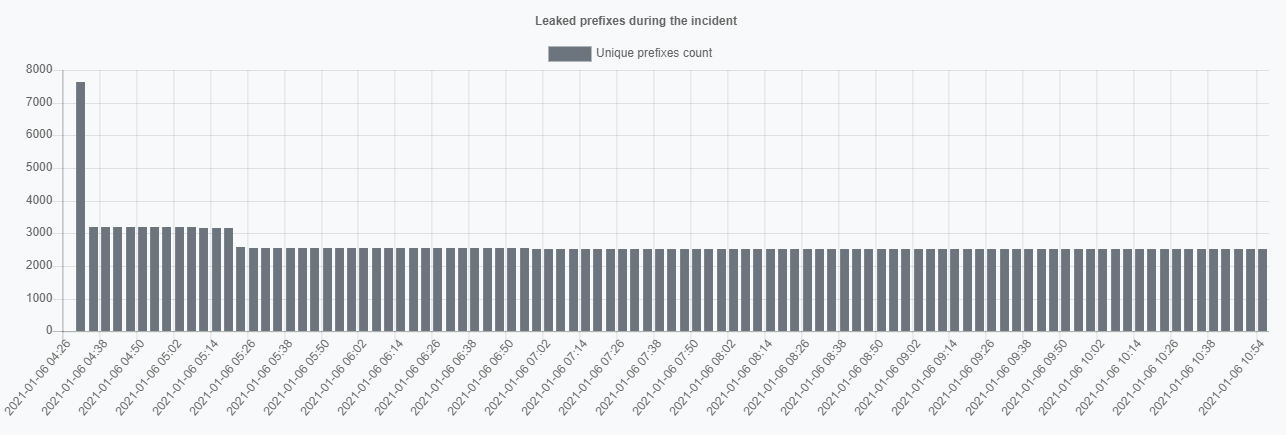
Starting at 4:21 UTC, AS9304 - a Hong Kong-based ISP HGC Global Communications Limited, leaked a tremendous, compared to average leak, amount of prefixes - 8764. Those contained IP-addresses of 907 ASNs from 66 countries, creating 9140 conflicts overall.
The active phase of this incident lasted for about 2.5 hours, shrinking afterwards.
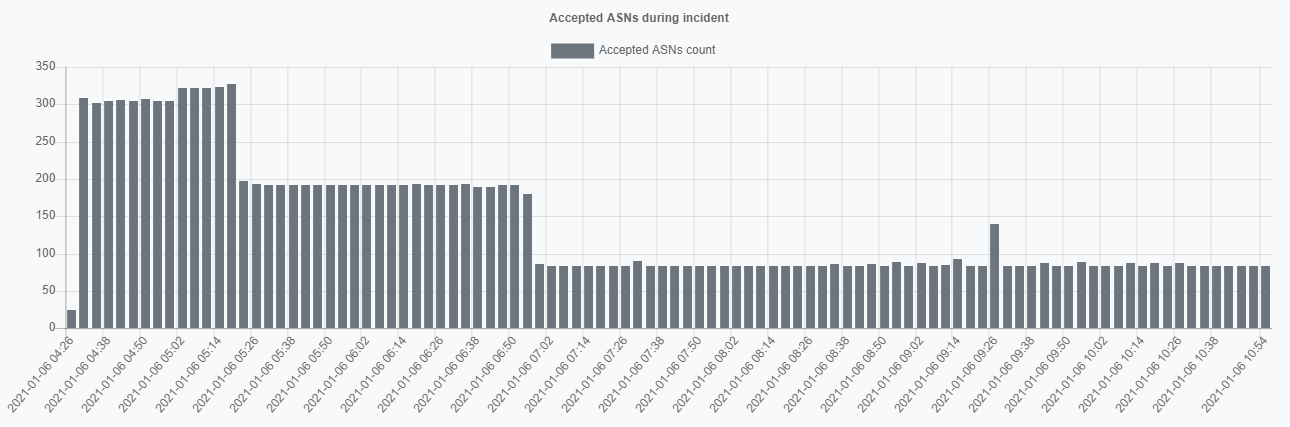
 If such a leak spreads globally, it would be a disastrous routing incident for everybody involved. By coincidence, this time, it hadn't happened. From our observation data, it turns out that only ⅓ of autonomous systems in leak accepted those prefixes.
If such a leak spreads globally, it would be a disastrous routing incident for everybody involved. By coincidence, this time, it hadn't happened. From our observation data, it turns out that only ⅓ of autonomous systems in leak accepted those prefixes.
Among the most affected by this particular route leak were EU and US prominent Internet transit actors, such as Akamai and Cloudflare. However, the leaked prefixes' scope was so broad that it is almost impossible for a company with a vast computer network not to be affected by such an incident.
Finally, for only 1% of the prefixes in the leak, the propagation was genuinely global. For the most part, this leak had limited worldwide visibility and reach. Which still could be rather dangerous and result in the loss of traffic and availability in certain regions.
UK-based AS15412 - belonging to Flag Telecom Global Internet - learned a precious lesson today. Now for this company's network engineers, there should be no further questions about the necessity of both ingress and egress prefix filtering.
