On April 23, 2020, an AS205310 leaked routes from one of its upstreams to another (from AS8220 to AS15943), affecting 90 000 prefixes.
In some cases, such an incident could lead to massive network degradation across dozens of ISPs. However, it did not. Why?
Because some companies install and maintain their filters properly. And even taking into regard the fact that AS15943 is directly connected to Tier-1 ISPs, they didn’t even notice the incorrect routes. They simply never reached Tier-1s, shrinking in size after each hop.
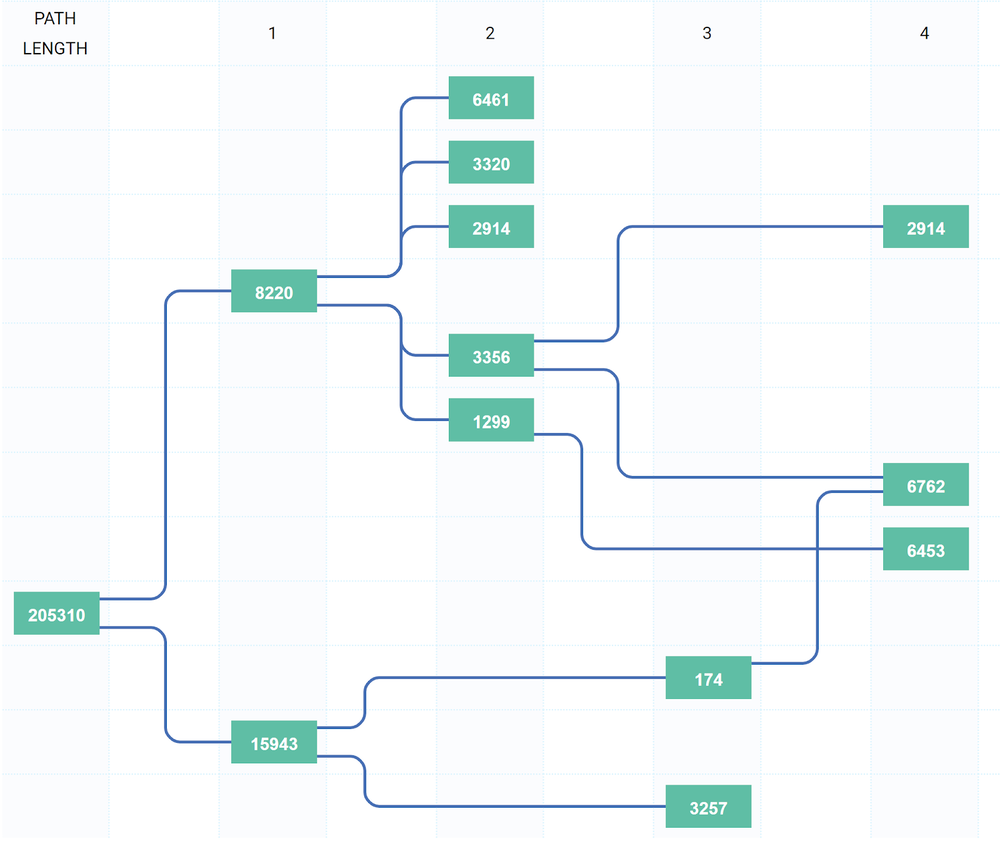
AS15943 has a very interesting AS-SET for the ISP that is so close to the Internet backbone. It consists of a small number of non-transit stabs. And it was only one ISP from AS15943 Customer Cone, whose prefixes were in AS205310 leak (with AS_PATH 15943 205310 8220 200183). It is interesting because these leaked prefixes were the only one accepted by Cogent (AS174).
as-set: AS-WTNET
descr: wilhelm.tel GmbH Norderstedt
remarks: wilhelm.tel GmbH Norderstedt
members: AS15943
remarks: Spiegel Verlag
members: AS199829
remarks: Marquard und Bahls
members: AS60264
remarks: Delaval
members: AS39268
remarks: Hauni
members: AS35391
remarks: Dokumenta
members: AS24657
remarks: Hansecom
members: AS199273
remarks: HHLA
members: AS50943
remarks: FidelioCruise
members: AS48355
remarks: Akquinet
members: AS35258
remarks: Content Fleet GmbH
members: AS200183
remarks: Bit-Serv
members: AS200978
remarks: MDEX
members: AS200567
remarks: AZV
members: AS49473
remarks: GLEICH Aluminium GmbH
members: AS204977
remarks: Beiersdorf Shared Services GmbH
members: AS205310
remarks: Serverleih
members: AS251
remarks: Kolle Rebbe GmbH
members: AS3573
remarks: Hermes
members: AS29042
remarks: X-ION
members: AS60664
remarks: HPA
members: AS210303
tech-c: WN136-RIPE
admin-c: WN136-RIPE
mnt-by: NORDERSTEDT-MNT
created: 2012-05-08T08:45:52Z
last-modified: 2020-02-13T14:36:19Z
source: RIPE
AS15943 AS-SET
We believe that because only a very few prefixes from AS15943 Customer Cone were leaked, some other Tier-1s (GTT for sure) could also not see this leak by applying prefix filtering based on AS-SETs or other grounds. The remaining part of Tier-1s didn’t see the leak, because they also have a direct connection with AS8220, and all these leaked prefixes were available through this operator in the routes with much shorter length of the AS_PATH than the leaked ones.
All these factors brought the next result. From 90 000 to 9 000 after the first two hops, which explains such a low propagation of such a voluminous route leak; and only 6000 could pass the country border and, for example looking from Moscow, Russia, only 2000 of leaker prefixes made it through. That is a vast difference from a route leak that happened previously, on April 22.
So the AS_SET-based filters work, as we can see in this particular example. We know that for sure with Cogent, GTT and, with high probability, for the rest of Tier-1s.
What is also weird with this route leak is that it consist only from ROA valid routes. So, exclusively the "drop Invalid" policy is not enough for BGP to be safe.
