Discover how cybercriminals use fast flux to increase the resilience and takedown immunity of their malicious infrastructure. Understand the benefits of fast flux for attackers, the challenges it presents for security professionals, and the most effective strategies for combating this threat, such as domain seizures, botnet takedowns, and international cooperation.

Cybercriminals are constantly refining their tactics to evade detection and sustain their malicious infrastructure, with fast flux emerging as a prominent technique. This method significantly boosts the resilience of botnets and malicious websites against takedown attempts. In this article, we will explore how fast flux works, why it poses a significant challenge to cybersecurity efforts, and how cybercriminals are capitalizing on this technique by selling fast flux infrastructure on cybercrime forums and networks.
Fast flux, a sophisticated DNS technique, rapidly alternates the IP addresses linked to a domain name, complicating the tracking and shutdown of malicious servers. Achieved through a botnet, a vast pool of compromised devices infected with malware, these devices become 'flux agents,' offering botnet protection and allowing attackers to control them, thus complicating efforts to combat malware and DDoS attacks.
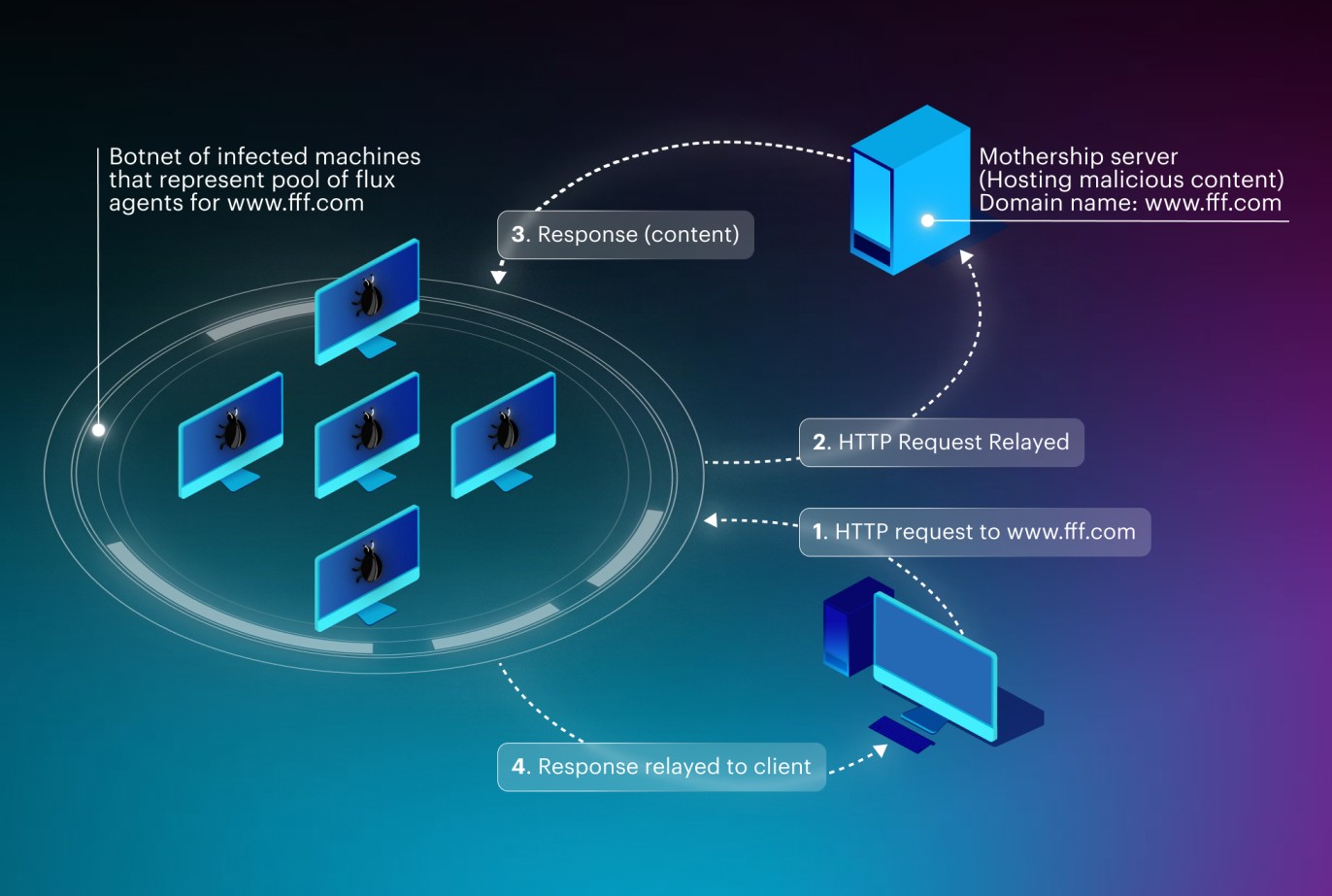
A basic illustration of how fast flux works
When a user attempts to access a malicious website utilizing fast flux, the domain name resolves to the IP address of a flux agent instead of the actual malicious server. This agent then forwards the user's request to the hidden server, relaying the response back. Employing different flux agents for each request significantly complicates the identification and blocking of the malicious server's location.
Fast flux networks can be classified into two types: single-flux and double-flux.
Single-flux networks modify the IP address linked to a single domain name, whereas double-flux networks also alter the IP addresses of the nameservers that resolve the domain name. Double-flux networks add an extra layer of obfuscation, enhancing the difficulty of tracing the malicious infrastructure.
Fast Flux Networks Remain Highly Resilient And Challenging To Take Down
The use of fast flux provides several benefits to cybercriminals.
Firstly, it enhances the availability of their malicious websites and botnets. By leveraging a diverse network of compromised devices acting as flux agents, attackers can distribute their malicious content across multiple locations, making it harder for security professionals to completely shut down the malicious activities. Such redundancy ensures that even if some agents are taken down, others can continue to operate, keeping the infrastructure active.

Evidence of a cybercrime market using fast flux
Secondly, fast flux helps cybercriminals evade detection from security solutions and law enforcement agencies. The constant rotation of IP addresses associated with the malicious domain names renders traditional blacklisting approaches largely ineffective. This rapid rotation of IP addresses also makes it challenging for security researchers and law enforcement to track and investigate the malicious infrastructure, providing cybercriminals with a window of opportunity to continue their activities unimpeded.
Additionally, employing a network of compromised devices as proxies obscures the true origin of attacks, complicating legal action by law enforcement. This technique, a critical aspect of network security, can also negatively impact legitimate users of the compromised devices.
For instance, if a home router becomes part of a fast flux botnet, it might still serve the household while being used for malicious purposes. Countermeasures against such compromised devices, crucial for network security, could inadvertently disrupt the legitimate online activities of unsuspecting users.
Cybercriminals Profit From Fast Flux By Selling Infrastructure-As-A-Service
Recognizing the value of fast flux, cybercriminals have started offering 'fast flux as a service' on cybercrime forums and networks. This development democratizes access to resilient, takedown-resistant networks, enabling a broader range of cybercriminals, including those with limited technical skills, to exploit this technique, underscoring the evolving challenges in network security.
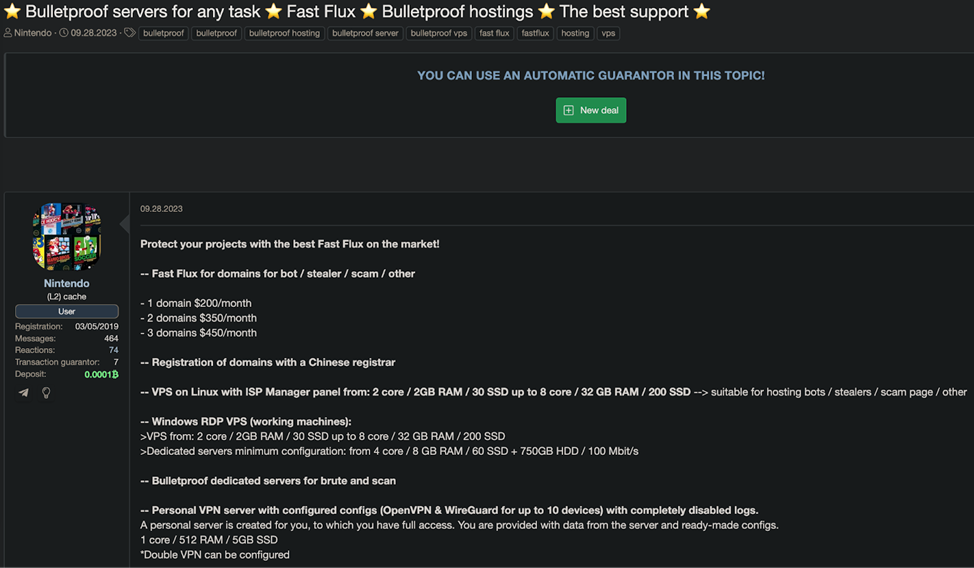
A cybercriminal selling fast flux as a service
The sale of fast flux infrastructure on cybercriminal forums and networks typically involves a subscription-based model, where buyers pay a recurring fee to access the fast flux network. The sellers often advertise their services based on the size of their botnet, the geographical distribution of their flux agents, and the uptime guarantees they provide. Some sellers even offer customization options, allowing buyers to specify the desired level of redundancy and the frequency of IP address rotation.
Domain Seizures Are the Most Effective Approach In Combating Fast Flux
To combat the malicious use of fast flux, the most effective approach is to focus on taking down or seizing the domain names associated with the malicious infrastructure. By disrupting the domain names, the fast flux network becomes ineffective, as the constantly changing IP addresses no longer have a stable domain to reference. Domain seizures require close collaboration between law enforcement agencies and domain registrars to quickly identify and suspend malicious domains.
A prime example of this approach is the takedown of the Avalanche network in 2016. Avalanche was a large-scale fast flux network that had been operating since 2009, causing an estimated €6 million in damages from concentrated cyberattacks on online banking systems in Germany alone. The global effort to take down this network involved the cooperation of law enforcement agencies from 30 countries, leading to the arrest of five individuals, the search of 37 premises, and the seizure of 39 servers.
The operation employed a technique called sinkholing, which involves redirecting traffic from malicious domains to a server controlled by law enforcement or security researchers, effectively neutralizing the malicious infrastructure. Impressively, the operation resulted in the seizure, sinkholing, or blocking of over 800,000 domains, making it the largest-ever use of sinkholing to combat botnet infrastructure at the time.
An example of a law enforcement seizure notice
However, domain seizures alone may not be sufficient to completely dismantle fast flux networks. Cybercriminals often use multiple domain names and can quickly register new ones to replace those that have been seized. A comprehensive strategy should also include efforts to identify and take down the underlying botnets that act as flux agents. This requires cooperation among international law enforcement agencies, as well as collaboration with internet service providers (ISPs) and cybersecurity firms to identify compromised devices.
Take Your Next Steps With Qrator Labs
Consider implementing an effective DNS security solution such as Qrator.SecureDNS to protect your organization from DNS-based attacks while also ensuring the availability and integrity of your DNS infrastructure.
Qrator.SecureDNS provides advanced mitigation techniques, a global anycast network for high availability, and simple deployment options that eliminate the need to fully disclose your domain zone. Organizations can reduce risks while maintaining visibility into their DNS traffic thanks to built-in DNSSEC support and detailed DNS traffic analysis. Click here to schedule a demo today and learn how we can help you.
