Last week there were several notable network incidents, which were the result of a new method for DDoS attacks amplification, using memcached database. Several DDoS mitigation providers, including Qrator Labs and Akamai, have confirmed that they were hit by this new attack kind. The new type of DDoS attack was able to break the record and reach 1.3 Tbps bandwidth. As a reaction to this new threat, Qrator.Radar team has added detection of the open-to-world memcached database in our daily scan.
Memcached by itself is in-memory key-value storage, which has simple goal - get the value for a selected key as fast as possible. This application uses both TCP and UDP on port 11211, and in some Linux-based operating systems by default listens to these ports on all interfaces. This created an opportunity for the attackers to:
- Inject a key with colossal value (50KB);
- Using IP spoofing create DDoS attack with almost unlimited amplification rate!
We created our scan by requesting stats method for the whole IPv4 address space. Of course, this kind of request does not show the possible rate of amplification, but we decided that we cannot inject any data into third-party databases, even with the proper intent. During previous week the number of vulnerable services has dramatically decreased.
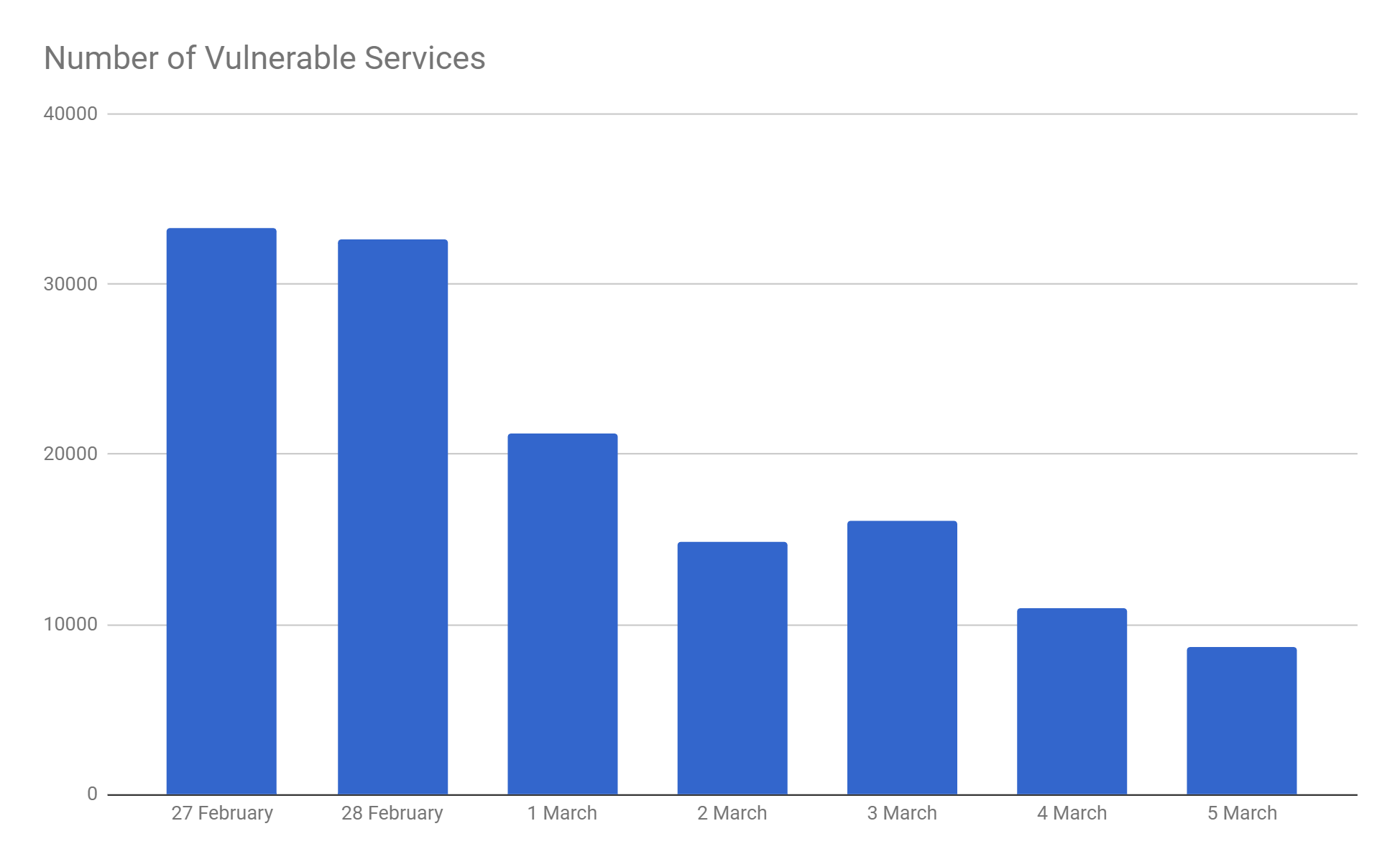
The significant part of this decrease was the result of homework made by several huge ISPs: AS37963 (Alibaba) -5223, AS16276 (OVH) -2388 and AS4134 (China Telecom) -1631. Still, there are more than 8000 services that haven’t been fixed. We encourage all ISPs to check their networks and fix services that can be used as amplification for the DDoS attack.
