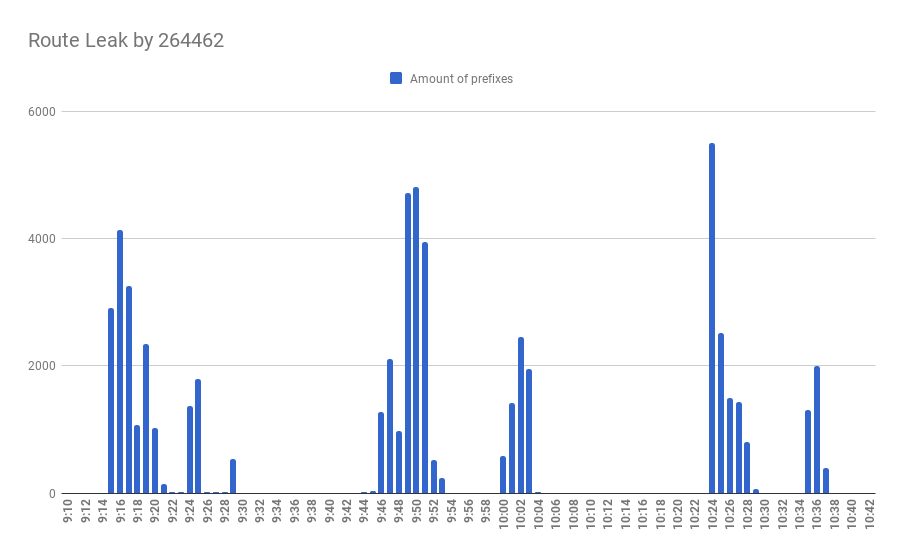
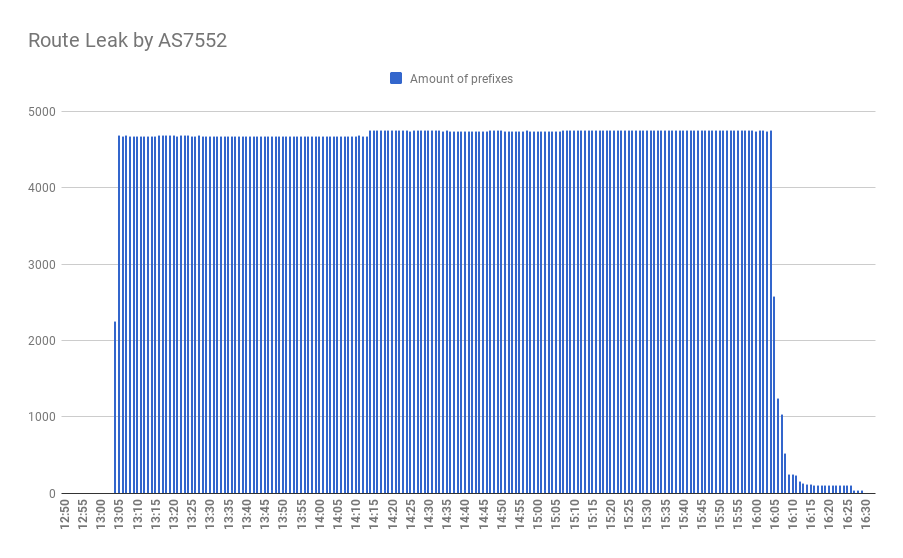
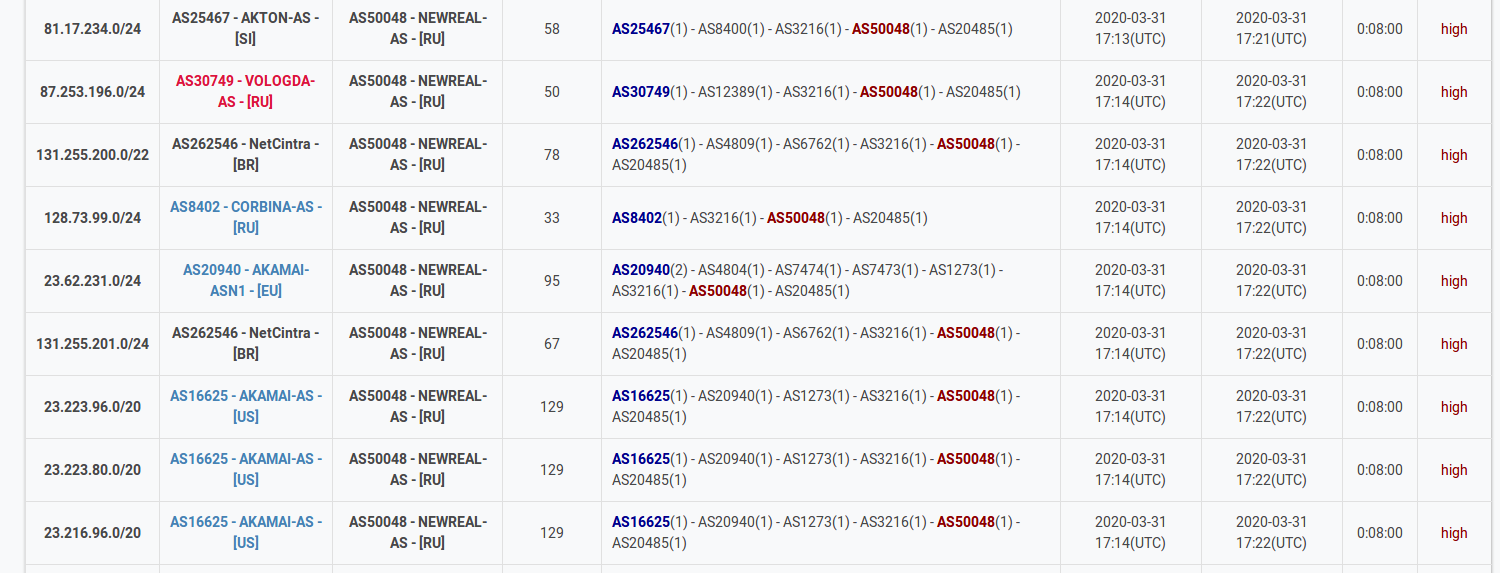
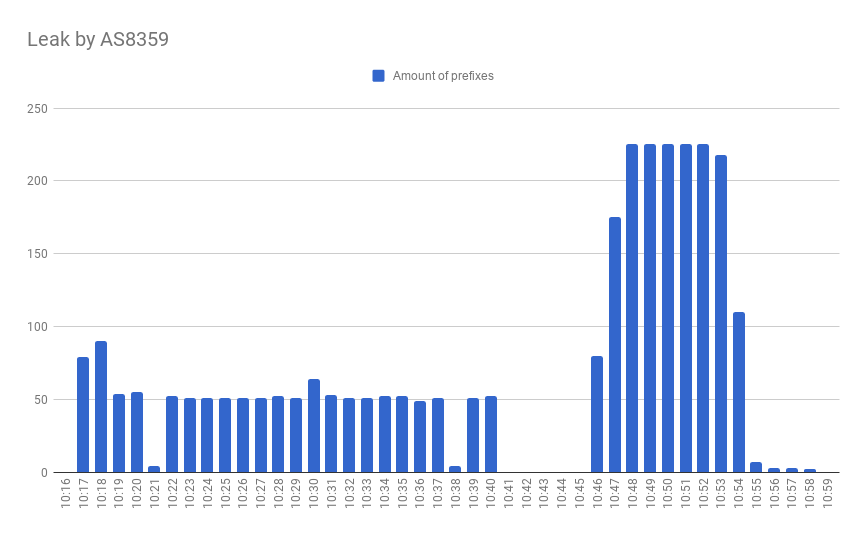
Today, on April 22, 2020, in the world of BGP routing, a thing that usually occurs in rare circumstances, happened. A year and 11 days ago, on April 11 2019, we wrote our first incident report about a thing that has never been observed before - a hijack by, with the highest probability, BGP optimizing software. Later that year, in summer, Cloudflare was brutally hit by the same type of incident. And today, a year after the first incident with AS263444 belonging to Open X Tecnologia Ltda, the same autonomous system… no, you guessed wrong.
Today it leaked 9328 prefixes from 1250 autonomous systems including all your favorite names: Akamai, Cloudflare, Vodafone, NTT, Amazon, NVIDIA and many others.
leaker | min_start_time | max_end_time | duration | prefix_count | origin_count | min_avg_max_propagation | max_duration
--------+------------------------+------------------------+----------+--------------+--------------+-------------------------+--------------
263444 | 2020-04-22 01:25:00+00 | 2020-04-22 01:47:00+00 | 00:22:00 | 9328 | 1250 | 2, 21, 176 | 00:22:00