Wow, that's been a week! Here's the blogpost copying our newsletter that covers all the newest information on what happened in cyber and network security from June 8 to June 13.

Wow, that's been a week! Here's the blogpost copying our newsletter that covers all the newest information on what happened in cyber and network security from June 8 to June 13.
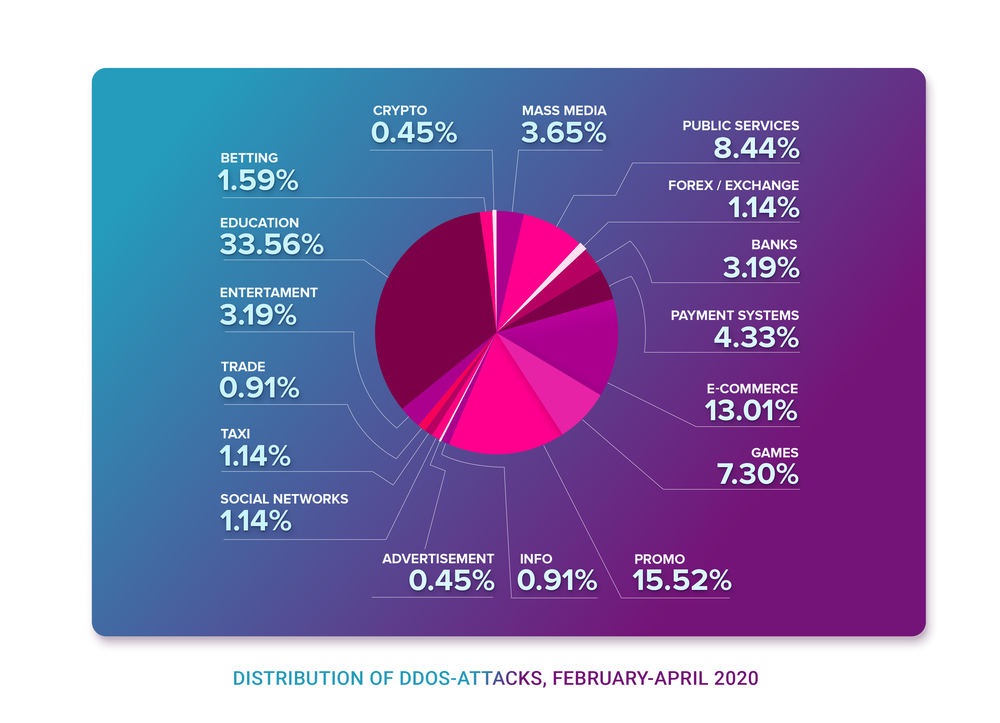
There would be no TL;DR in this article, sorry.
Those have been three months that genuinely changed the world. An entire lifeline passed from February, 1, when the coronavirus pandemics just started to spread outside of China and European countries were about to react, to April, 30, when nations were locked down in quarantine measures almost all over the entire world. We want to take a look at the repercussions, cyclic nature of the reaction and, of course, provide DDoS attacks and BGP incidents overview on a timeframe of three months.
In general, there seems to be an objective pattern in almost every country’s shift into the quarantine lockdown.
On April 23, 2020, an AS205310 leaked routes from one of its upstreams to another (from AS8220 to AS15943), affecting 90 000 prefixes.
In some cases, such an incident could lead to massive network degradation across dozens of ISPs. However, it did not. Why?
Because some companies install and maintain their filters properly. And even taking into regard the fact that AS15943 is directly connected to Tier-1 ISPs, they didn’t even notice the incorrect routes. They simply never reached Tier-1s, shrinking in size after each hop.
Today, on April 22, 2020, in the world of BGP routing, a thing that usually occurs in rare circumstances, happened. A year and 11 days ago, on April 11 2019, we wrote our first incident report about a thing that has never been observed before - a hijack by, with the highest probability, BGP optimizing software. Later that year, in summer, Cloudflare was brutally hit by the same type of incident. And today, a year after the first incident with AS263444 belonging to Open X Tecnologia Ltda, the same autonomous system… no, you guessed wrong.
Today it leaked 9328 prefixes from 1250 autonomous systems including all your favorite names: Akamai, Cloudflare, Vodafone, NTT, Amazon, NVIDIA and many others.
leaker | min_start_time | max_end_time | duration | prefix_count | origin_count | min_avg_max_propagation | max_duration
--------+------------------------+------------------------+----------+--------------+--------------+-------------------------+--------------
263444 | 2020-04-22 01:25:00+00 | 2020-04-22 01:47:00+00 | 00:22:00 | 9328 | 1250 | 2, 21, 176 | 00:22:00
On Sunday of April 5, 2020, only a few days after last week route leaks an AS7552 belonging to Viettel - according to Wikipedia the largest telecommunication service provider in Vietnam - was leaking routes for more than 3 hours in a row.
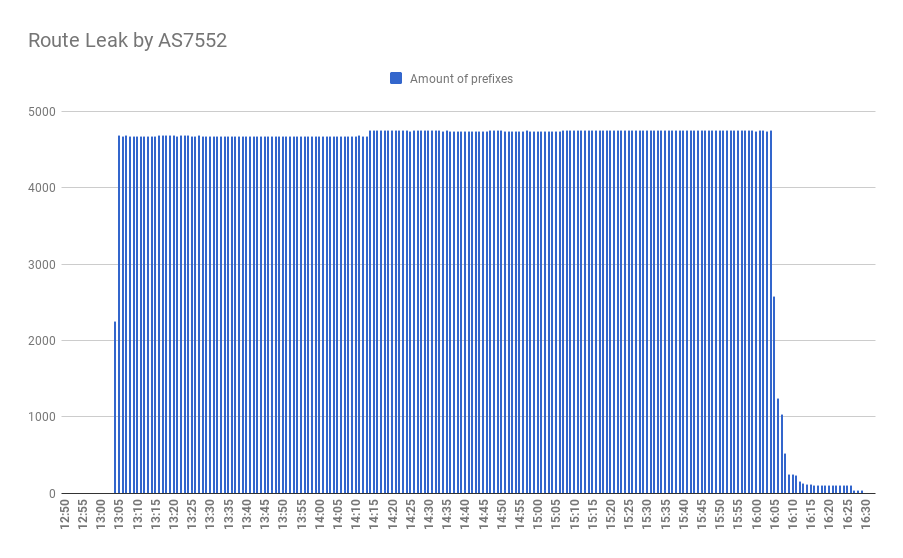
The leak affected 4825 network prefixes from 326 operators, spreading from AS7552 upstreams: AS3491 and AS4637 towards AS1273 - Vodafone, which helped spread it to almost all major Tier-1 ISPs. Most of all Vietnamese, Cambodian and Australian networks were affected, with more than 25% of ISPs in the first two countries.
That, we must say, is the unique story so far.
Here’s the beginning: for approximately an hour, starting at 19:28 UTC on April 1, 2020, the largest Russian ISP — Rostelecom — was announcing prefixes belonging to prominent internet players: Akamai, Cloudflare, Hertzner, Digital Ocean, Amazon AWS, and other famous names.
Before the issue was resolved, paths between the largest cloud networks were somewhat disrupted — the Internet blinked. The route leak was distributed quite well through Rascom (AS20764), then Cogent (AS174) and in a couple of minutes through Level3 to the world. The issue suddenly became bad enough that it saturated the route decision-making process for a few Tier-1 ISPs.
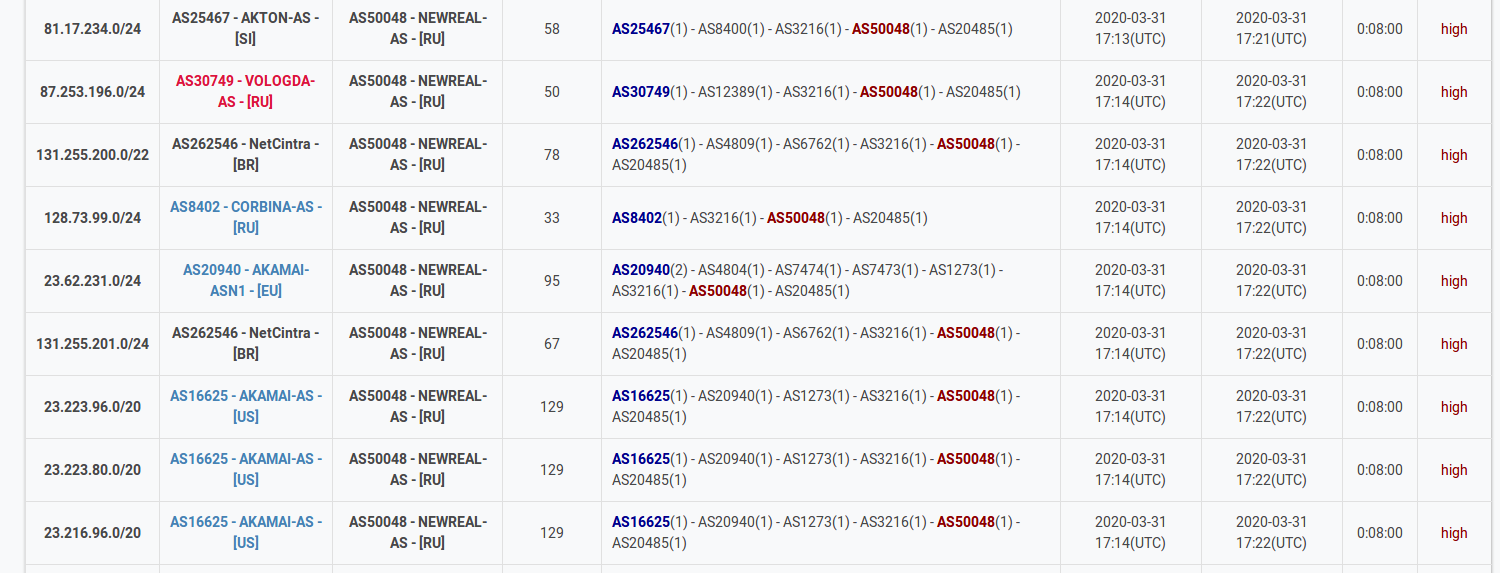
At 17:13 UTC on March 31, 2020, the AS50048 (NEWREAL-AS) leaked, in total, 2658 IPv4 network prefixes to the Tier-2 transit provider Transtelecom. Those prefixes included Orange, Akamai, Rostelecom and more than 300 other companies’ networks.

Established in 2009, Qrator Labs provides DDoS mitigation services and is an acknowledged expert in this industry. The Qrator Labs expert team has been conducting research in the field of DDoS protection since 2006 and has been continuously improving algorithms, technologies and techniques of DDoS attack mitigation. In 2010 the company launched its own Qrator traffic filtration network as a technological basis for the commercial service dedicated to the protection of network services from similar threats. Algorithms and technologies used for mitigation of attacks against the web services of its customers are the company’s specialty and focus.
“In 1665, Cambridge University closed because of the plague. Issac Newton decided to work from home. He discovered calculus & the laws of motion.”
We live in a truly remarkable moment. With the year 2020 and the COVID-19 outbreak employees all over the world are staying home for quarantine, trying their best to sustain the normal flow of life, which means continue working. And this is something new compared to all the previous infectious pandemics humanity has survived through — this time we have the Internet.
 Closely watched events of 2019
Closely watched events of 2019