Before we start investigating what is happening with the Internet within and outside of Belarus, let us quote a couple of sentences we are repeating in annual National Reliability Research & Report:
“Strictly speaking, when the BGP and the world of interdomain routing were in the design stage, the creators assumed that every non-transit AS would have at least two upstream providers to guarantee fault tolerance in case one goes down. However, the reality is different; over 45% of ISP’s have only one connection to an upstream transit provider. A range of unconventional relationships among transit ISPs further reduces reliability. So, have transit ISPs ever failed? The answer is yes, and it happens with some frequency. The more appropriate question is — under what conditions would a particular ISP experience service degradation? If such problems seem unlikely, it may be worth considering Murphy’s Law: “Anything that can go wrong, will.”
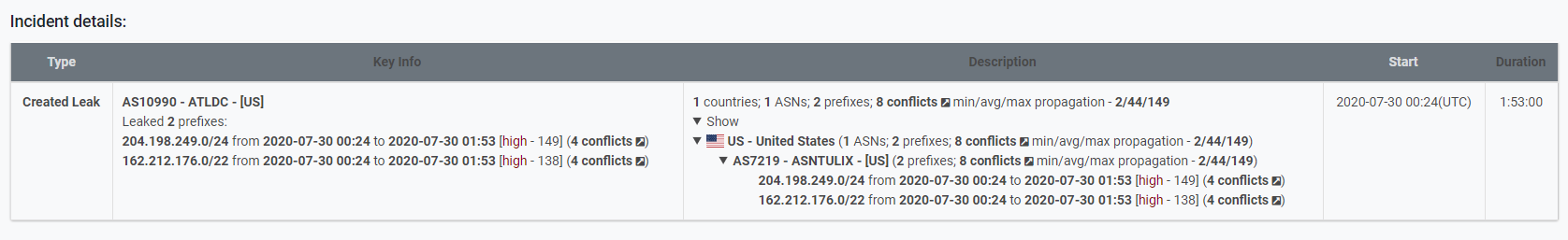
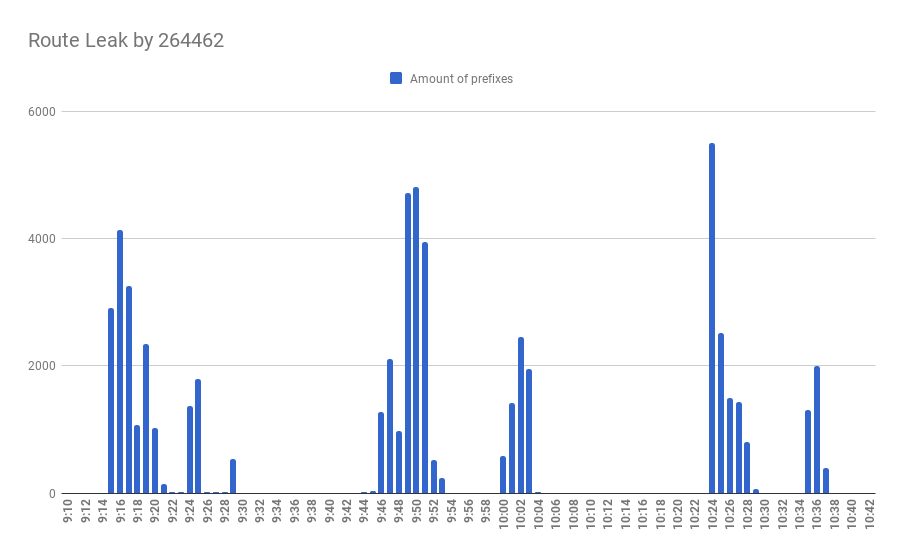
Why are we repeating this rather than start with the facts and timesteps as usual? Because this is precisely the case, from our point of view, with Belarus’ internet segment. Let us take a look at two diagrams representing a BGP network of Belarus a month ago, at the beginning of July 2020: