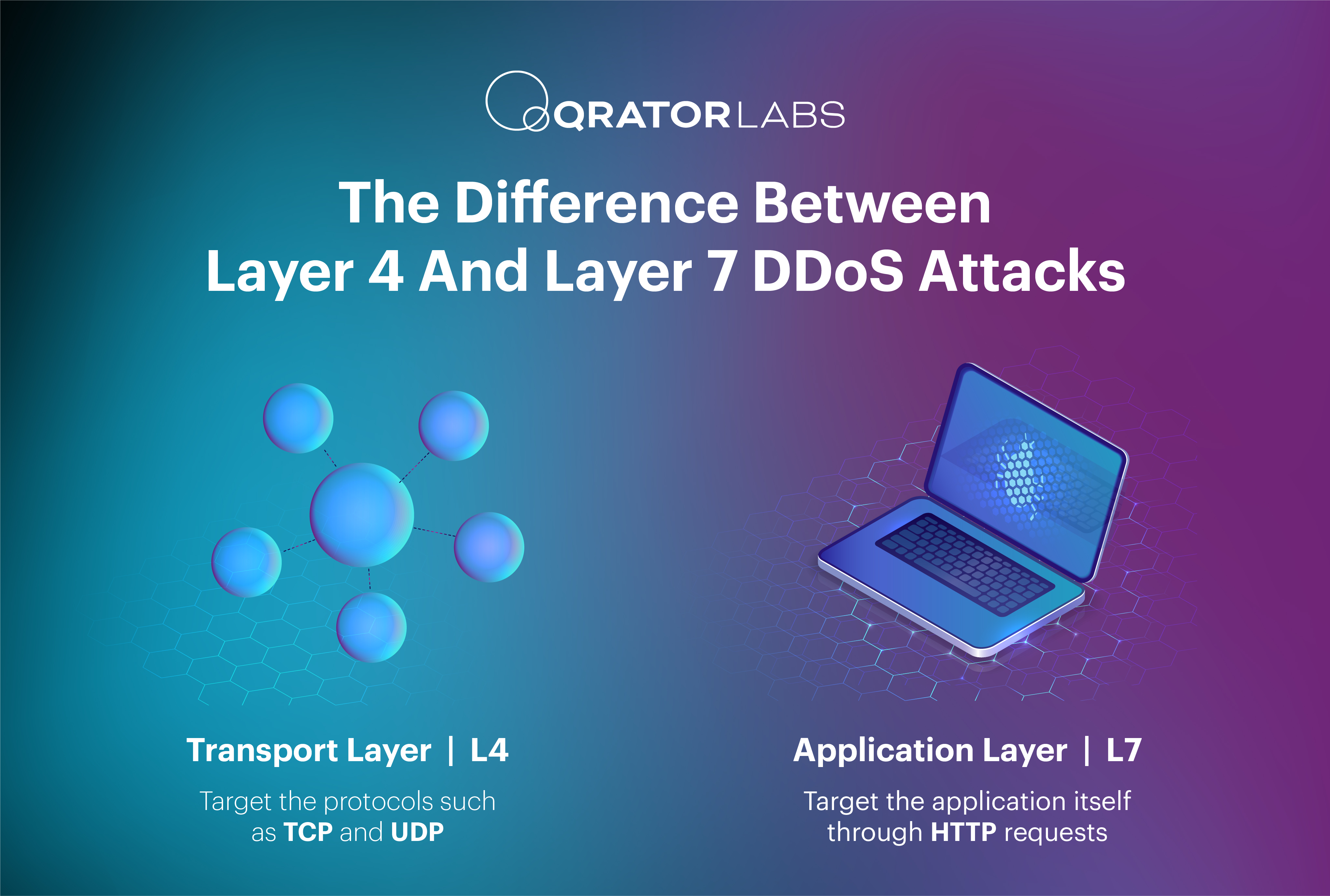
Recent years have seen distributed denial-of-service (DDoS) attacks grow larger and happen more often than ever before. In just the first three months of 2025, the number of DDoS attacks worldwide increased by 110% compared to the same period the year before.
One late-March incident involved a botnet of 1.33 million compromised devices, almost six times larger than the biggest botnet observed the year prior. That botnet blitzed an online betting platform, and over half of the attacking devices originated from a single country (Brazil). In the following quarter, its size grew to 4.6 million devices, and by the next quarter, it reached 5.76 million.