Hello, everybody!

My name is Alexander Zubkov and today I’d like to talk about routing loops.
Hello, everybody!

My name is Alexander Zubkov and today I’d like to talk about routing loops.

Introduction
For the last five years, there have virtually been almost no global-scale application-layer attacks.
During this period, the industry has learned how to cope with the high bandwidth network layer attacks, including amplification-based ones. It does not mean that botnets are now harmless.
End of June 2021, Qrator Labs started to see signs of a new assaulting force on the Internet – a botnet of a new kind. That is a joint research we conducted together with Yandex to elaborate on the specifics of the DDoS attacks enabler emerging in almost real-time.
Among many popular graph algorithms, several algorithms allow you to find the shortest paths. Each of them solves its own problem and, accordingly, has its own application in practice. For example, the A* search algorithm can use various heuristics to find the path of the minimum cost in video games, while the Floyd — Warshell algorithm allows you to efficiently find the shortest paths between all pairs of vertices in dense graphs and can be used in the Schultz method to determine the winner of the election [1]. However, computer networks are considered to be the area where shortest path algorithms are strongly sought-for.
This article by Roman Klimovitsky describes how such problems arise in Qrator Labs and how we solve them.
For several years now, Qrator Labs has been working with different universities to find students interested in specific tasks we deal with, for them to either get new experience or mark a future career path in network and computer engineering.
At the moment, several Qrator Labs employees started out as interns, picking one of the programs provided at the universities they studied. Of course, not everyone chooses computer engineering as a field of specialization — out of 23 students that participated in the university programs during 2019 and 2020, 9 were invited for internships. Only four of them became our colleagues in those years, which makes their stories quite special.
In one of our previous publications, we talked about a way to measure event stream rate using a counter based on exponential decay. It turns out that the idea of such a counter has an interesting generalization.
Our immersion plan is as follows. First, let us look at and analyze a few examples of how events are counted and the rate of the stream is estimated in general. The next step is to see a generalization, namely some class of counters, which we call the u-model. Next, we explore what useful properties u-models have and propose a technique for constructing an adequate rate estimate.
We are glad to present you an article written by Qrator Labs' engineer Dmitry Kamaldinov. If you want to be a part of our Core team, write us at hr@qrator.net.
On implementing streaming algorithms, counting of events often occurs, where an event means something like a packet arrival or a connection establishment. Since the number of events is large, the available memory can become a bottleneck: an ordinary \(n\)-bit counter allows to take into account no more than \(2^n - 1\) events.
One way to handle a larger range of values using the same amount of memory would be approximate counting. This article provides an overview of the well-known Morris algorithm and some generalizations of it.
Another way to reduce the number of bits required for counting mass events is to use decay. We discuss such an approach here, and we are going to publish another blog post on this particular topic shortly.
In the beginning of this article, we analyse one straightforward probabilistic calculation algorithm and highlight its shortcomings (Section 2). Then (Section 3), we describe the algorithm proposed by Robert Morris in 1978 and indicate its most essential properties and advantages. For most non-trivial formulas and statements, the text contains our proofs, the demanding reader can find them in the inserts. In the following three sections, we outline valuable extensions of the classic algorithm: you can learn what Morris's counters and exponential decay have in common, how to improve the accuracy by sacrificing the maximum value, and how to handle weighted events efficiently.
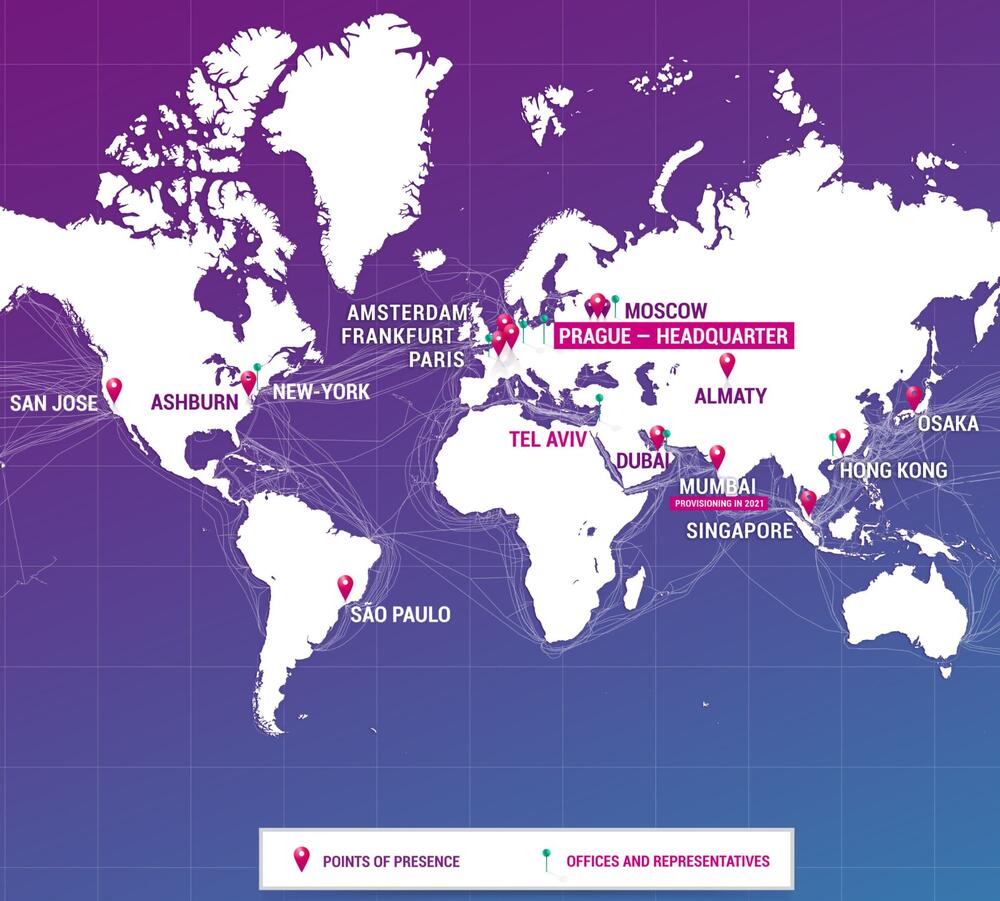
Why is it valuable to get into the Qrator Labs partnership program?
In Qrator Labs, we firmly believe that working together brings a better result. Which is the reason why, for years, we were trying to find meaningful partnerships with all kinds of companies. They either seek to provide their existing customers with the top-notch DDoS mitigation technology developed at Qrator Labs with many additional ecosystem solutions or want to succeed the other way around. By getting their product available for Qrator Labs' customers by integrating into the Qrator anycast filtering network.
Greetings, fellow newsletter subscriber! Once again, we are back with the best stories and articles published on the topic of cybersecurity in two weeks, between 14 and 28 February, the year 2021.

Hello and welcome back to the regular cyber and infosecurity letter! This time we are going through the relevant articles published 8 - 14 February 2021.

Greetings, fellow subscribers! As usual on Sundays, we are back with the most relevant and interesting articles published between February 1 and 7, 2021.